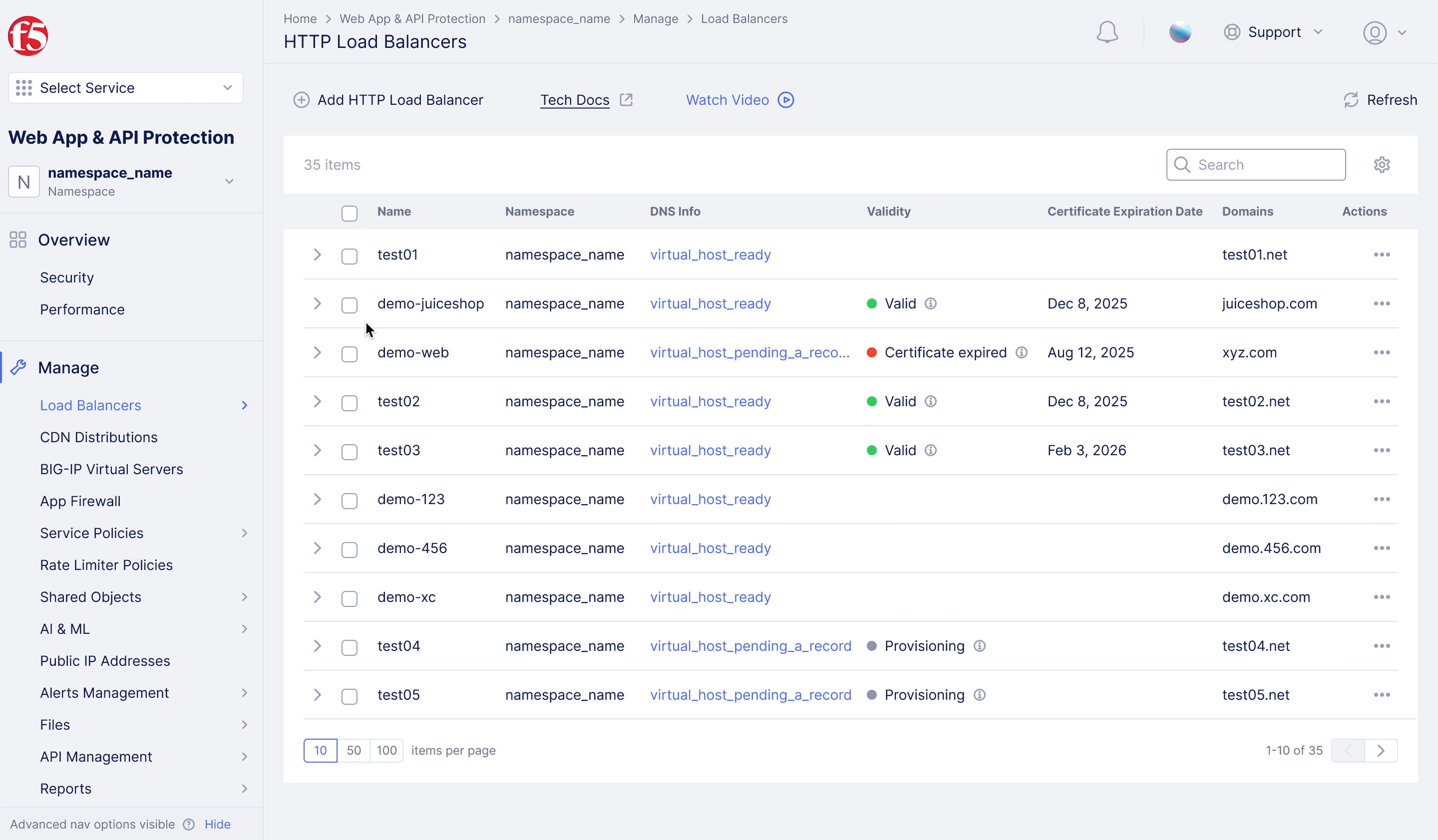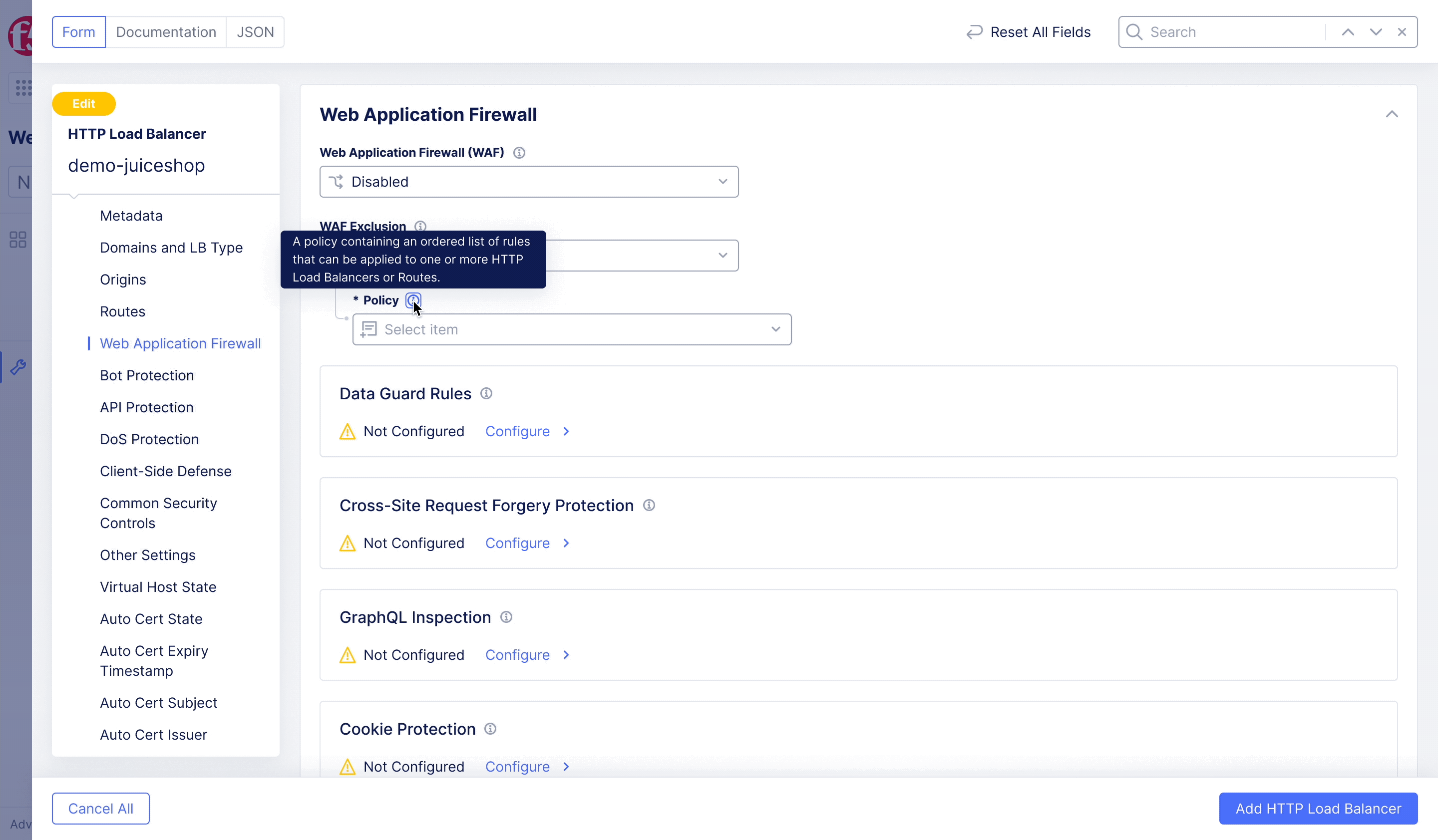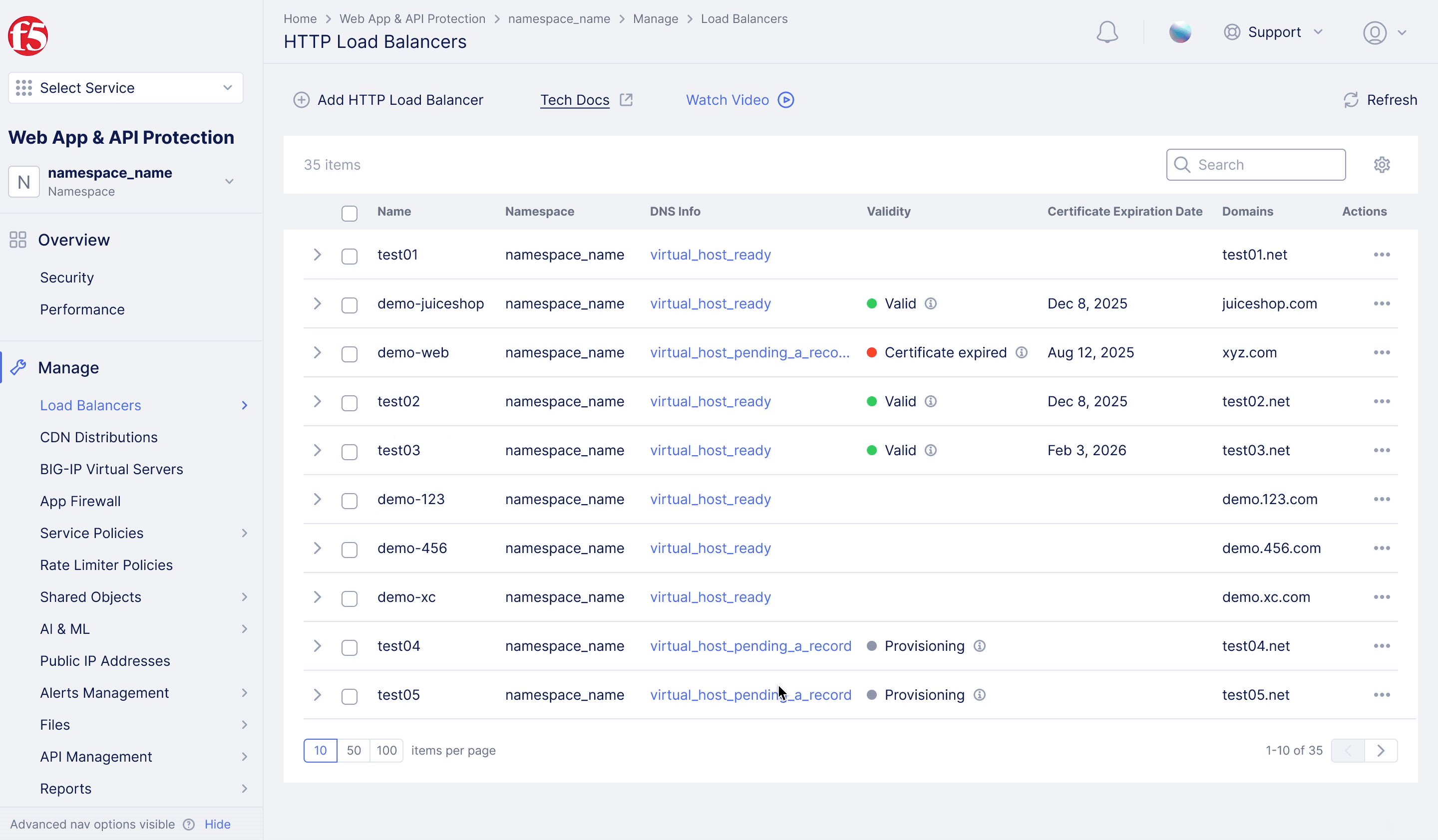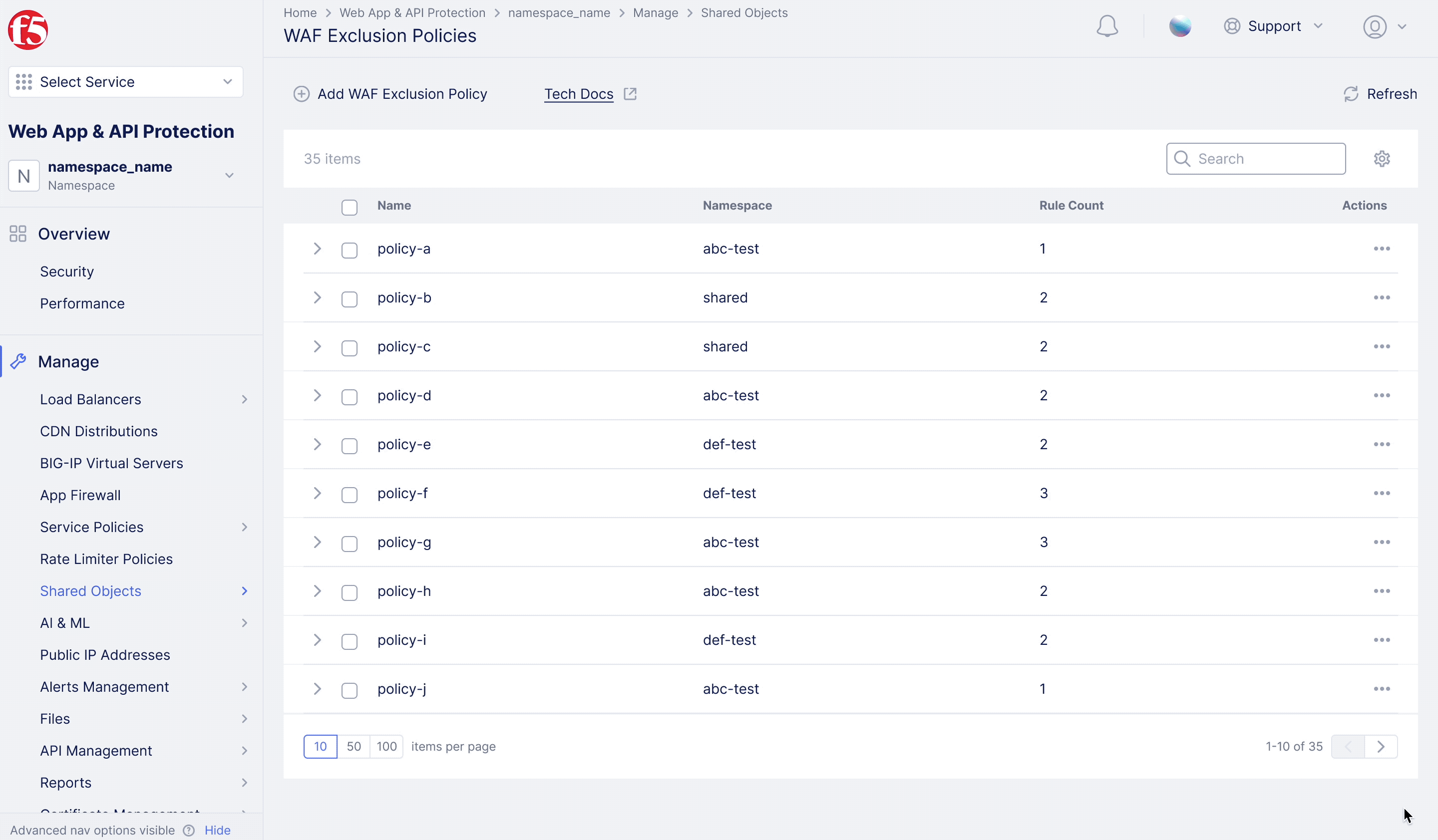
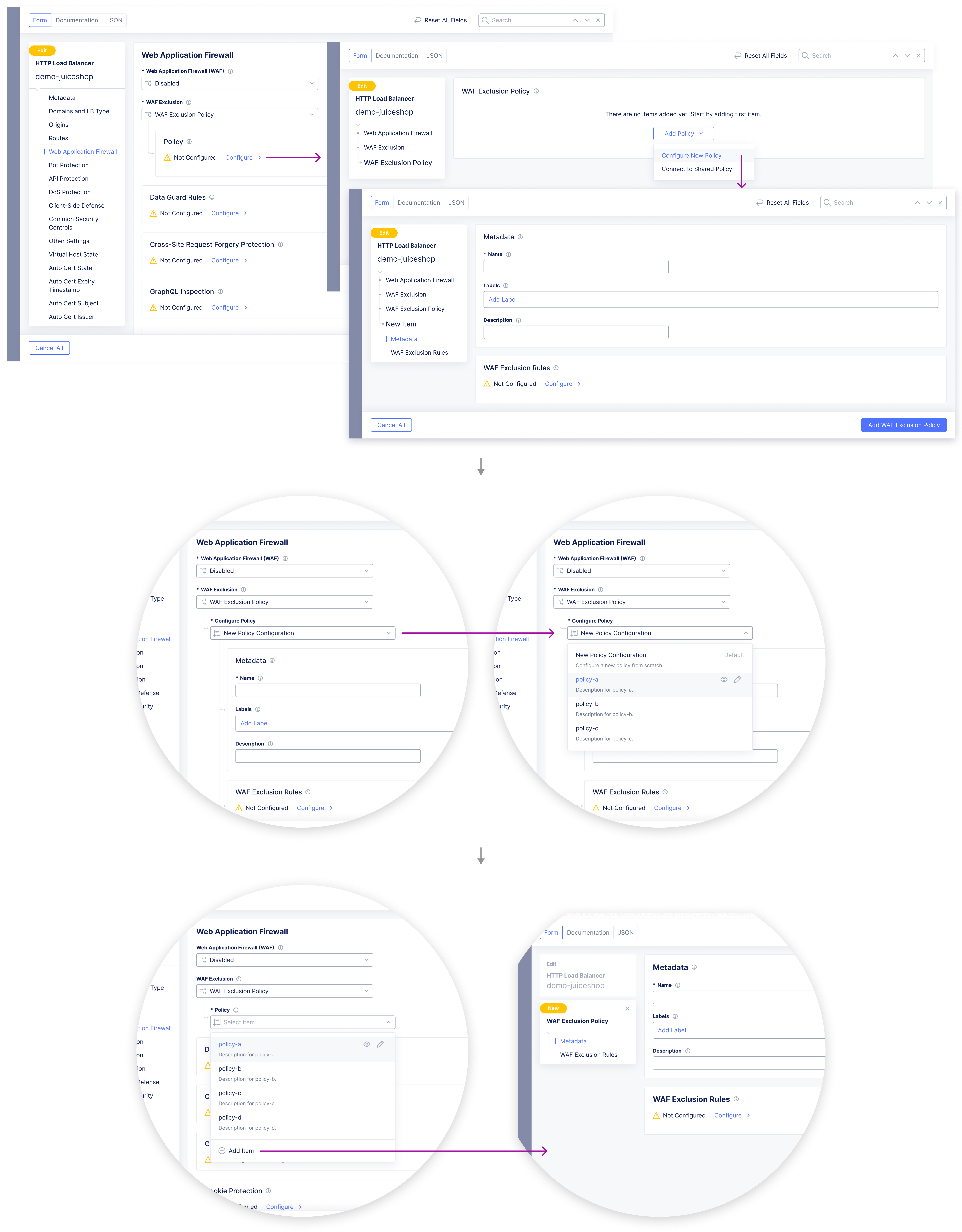
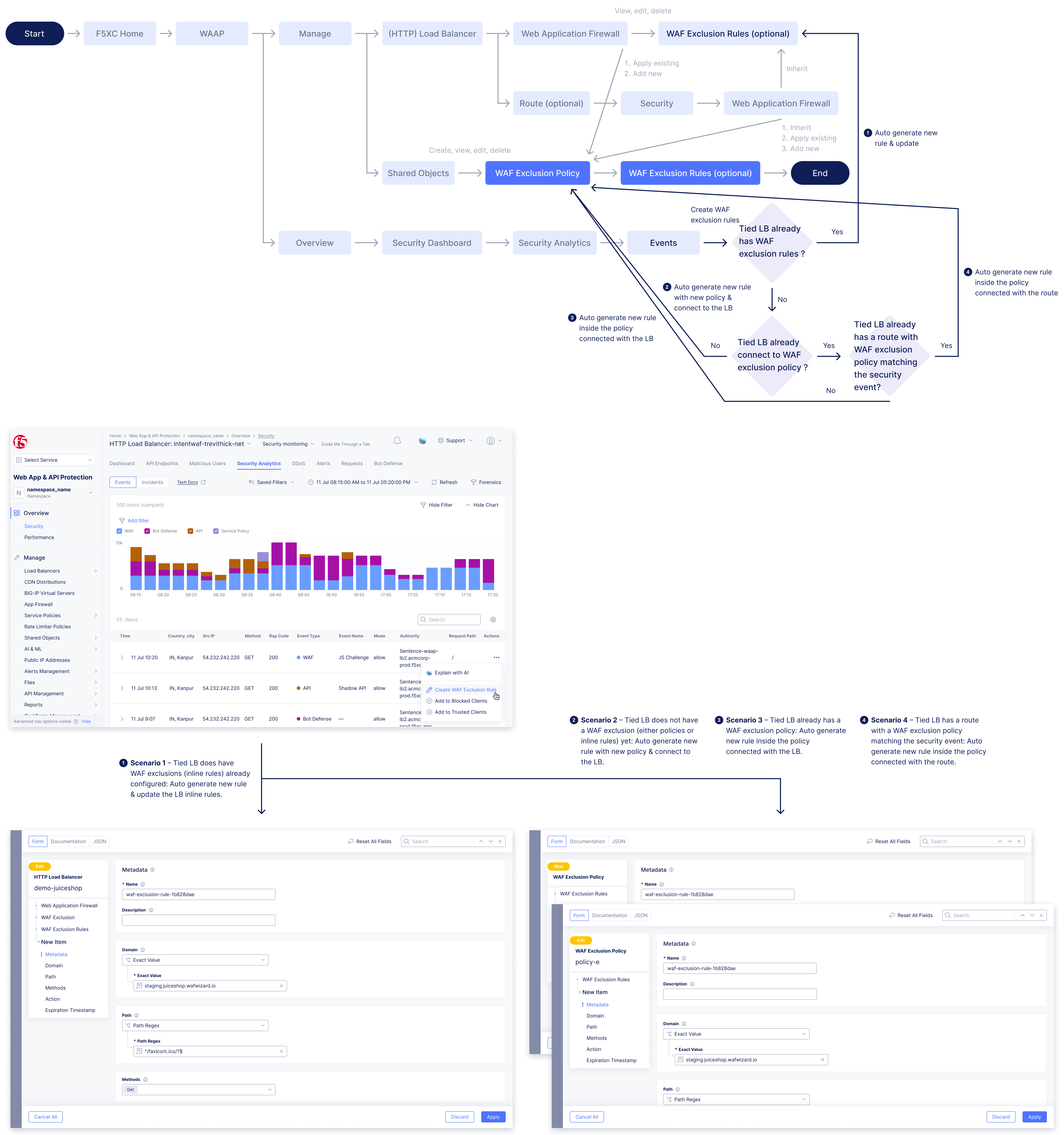
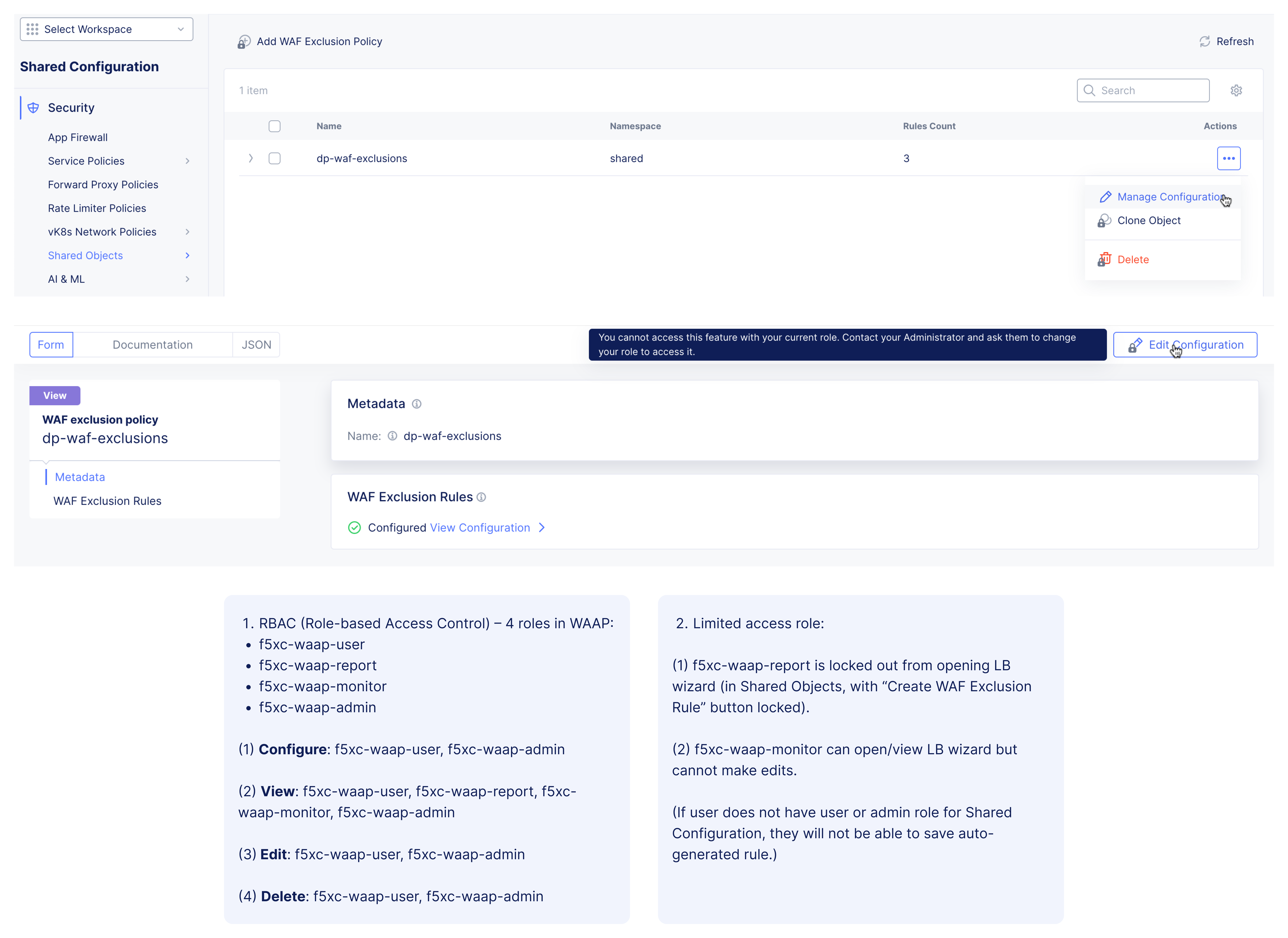
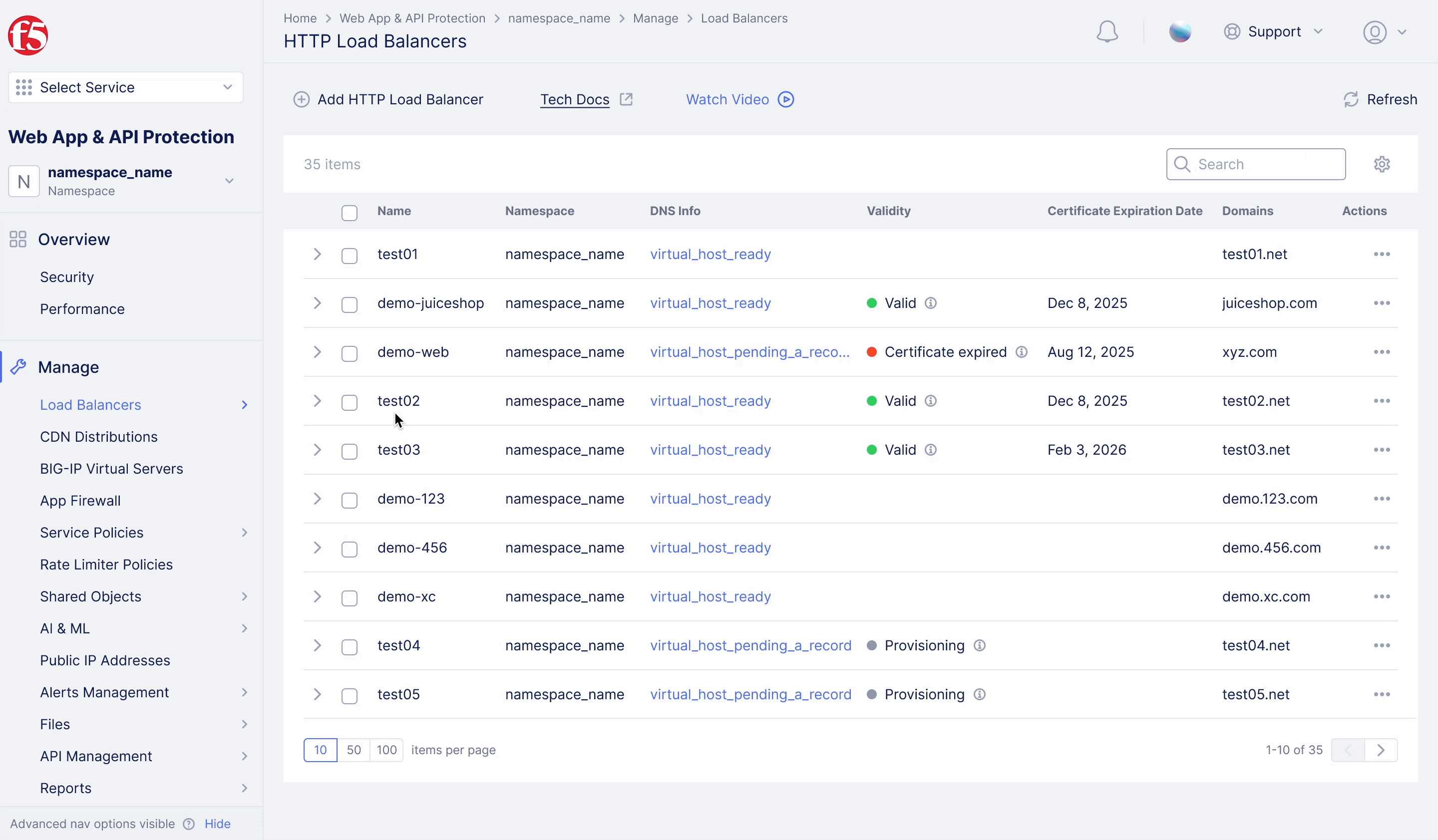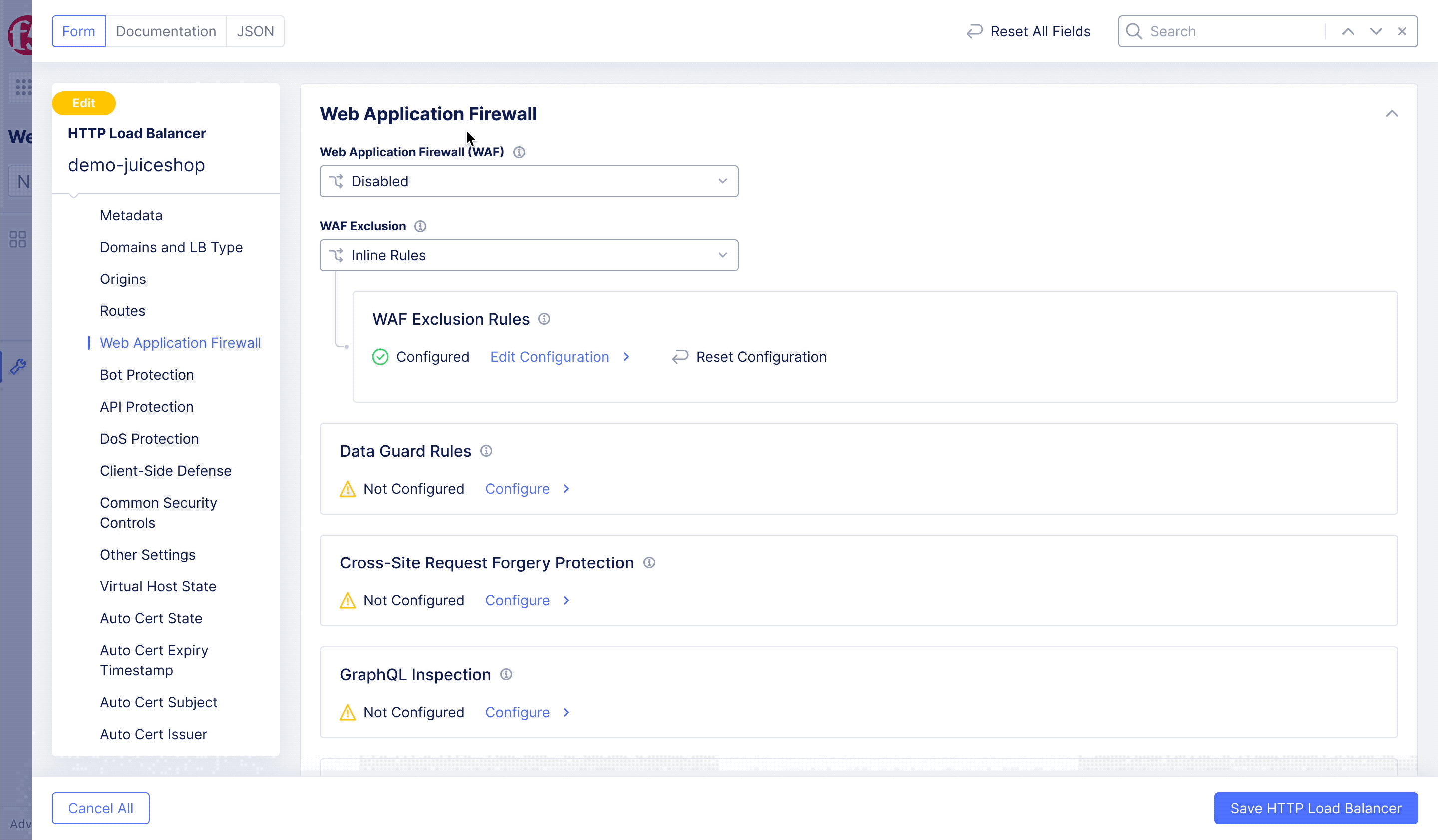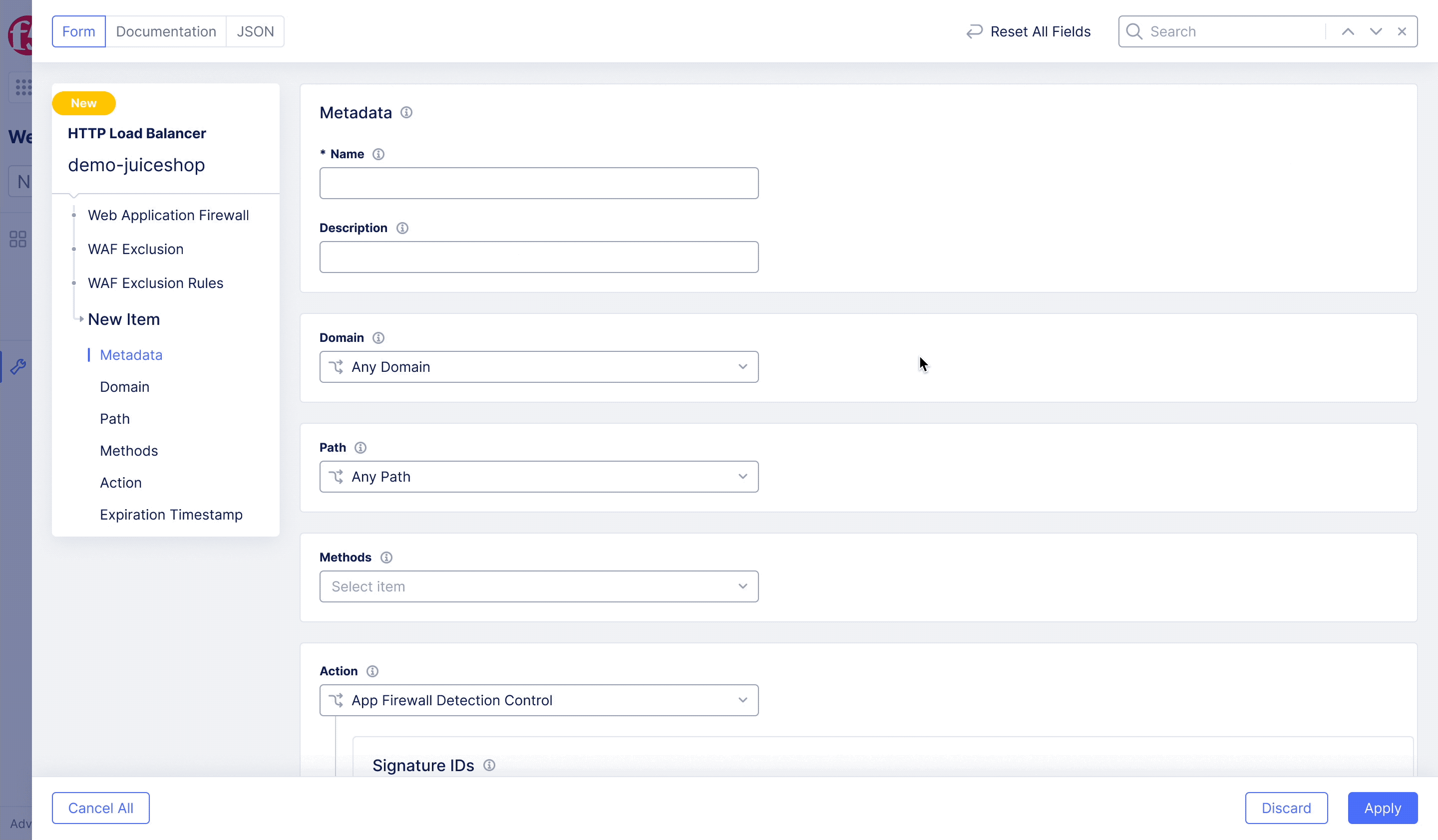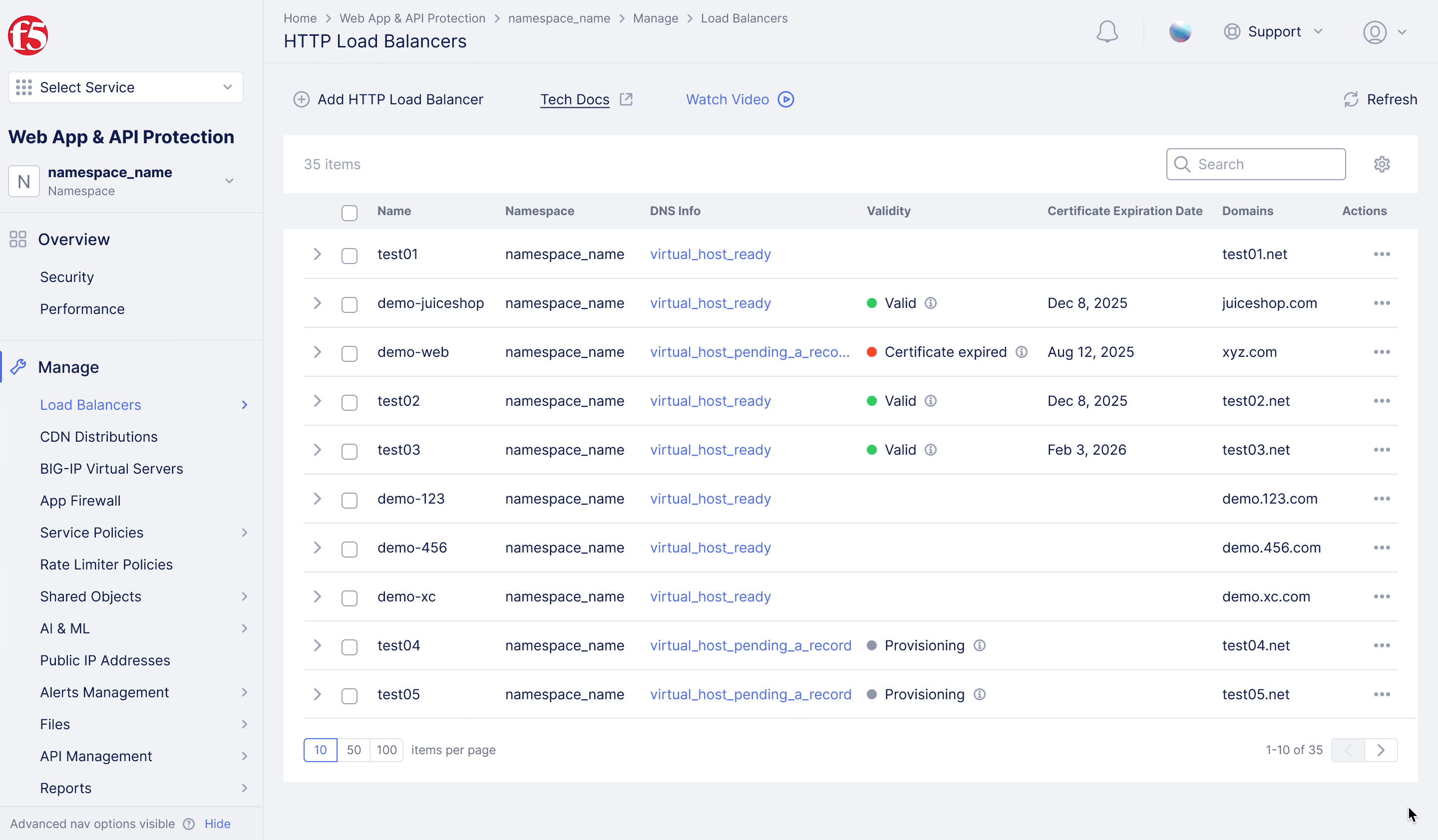
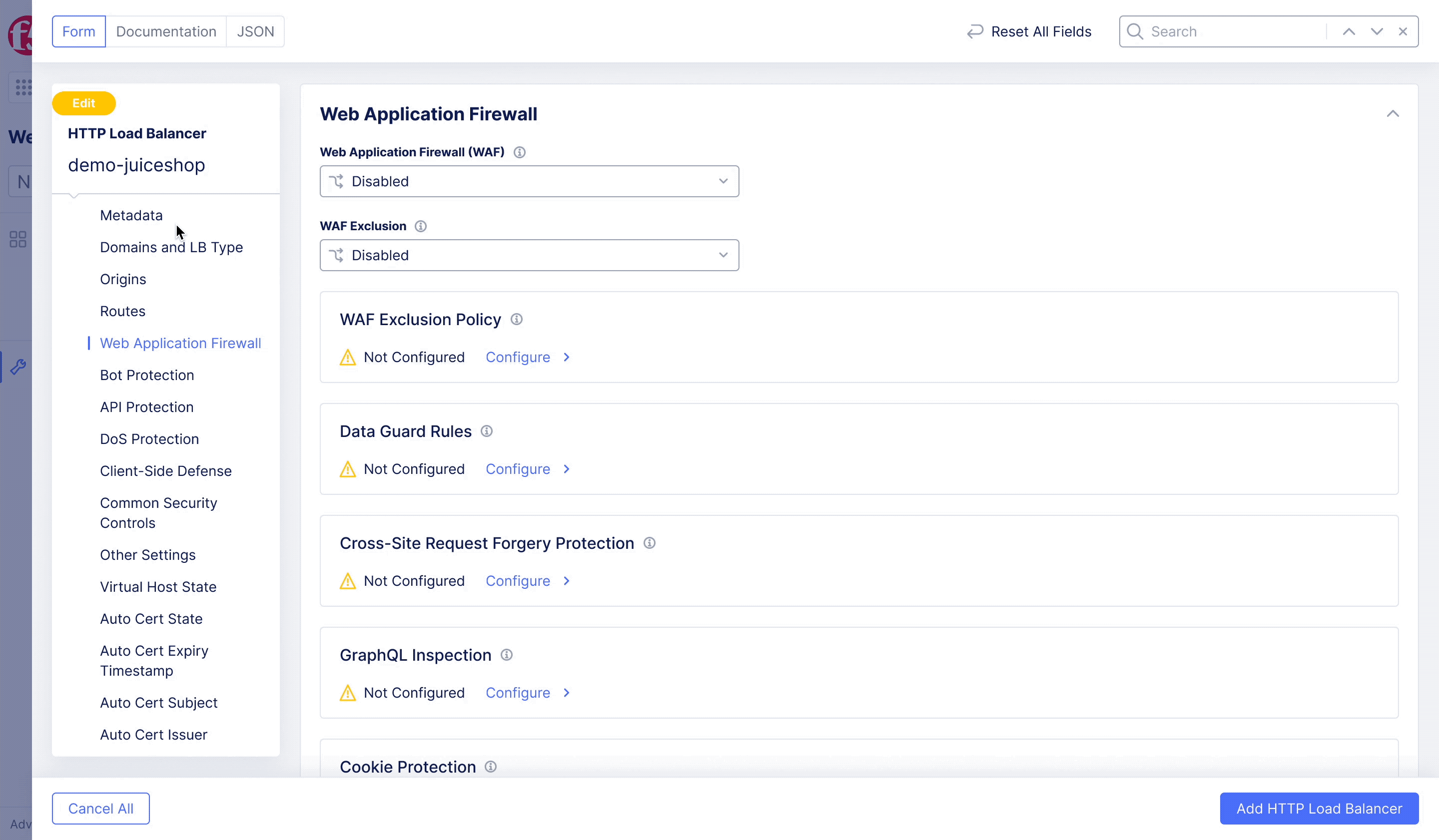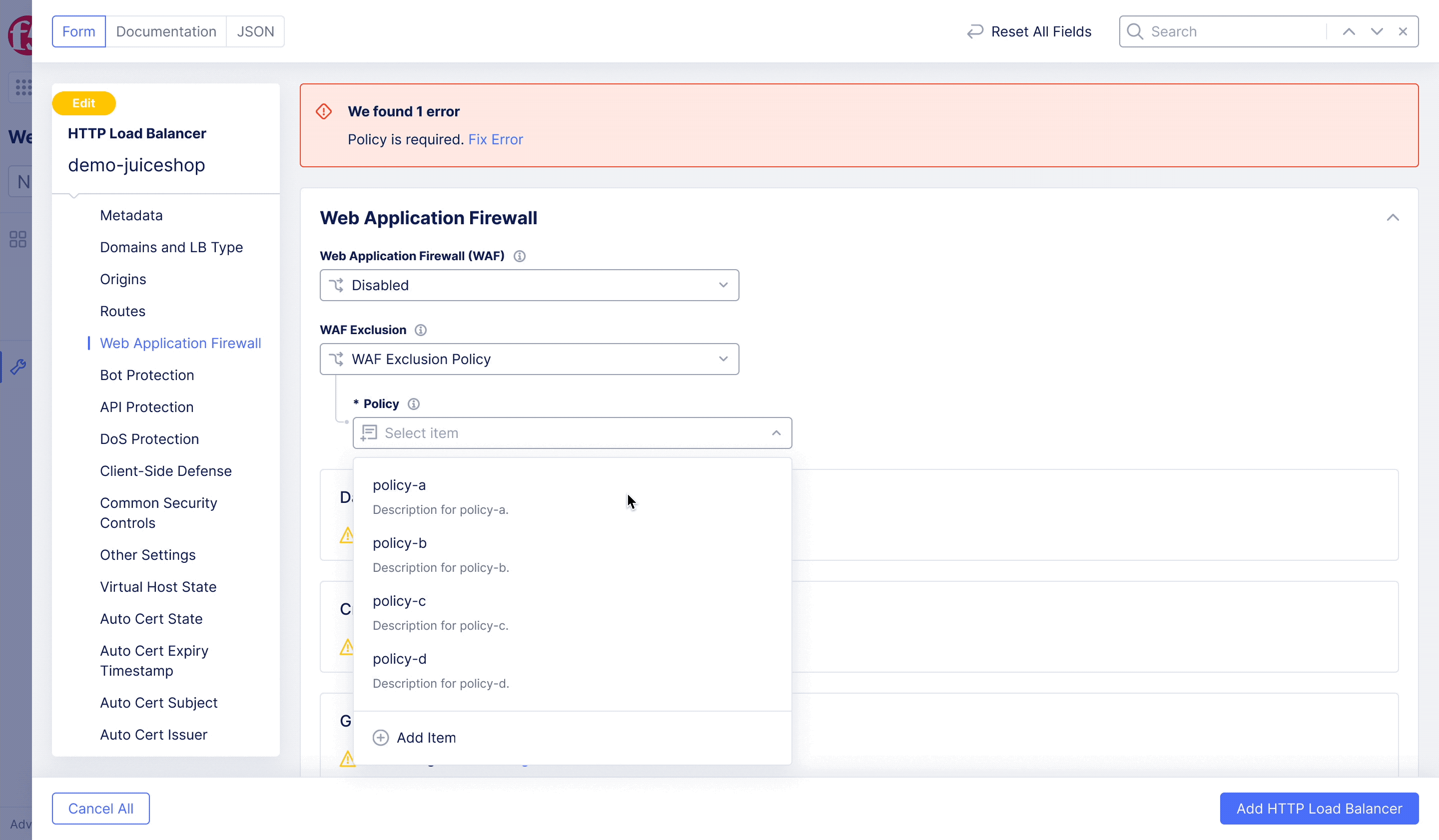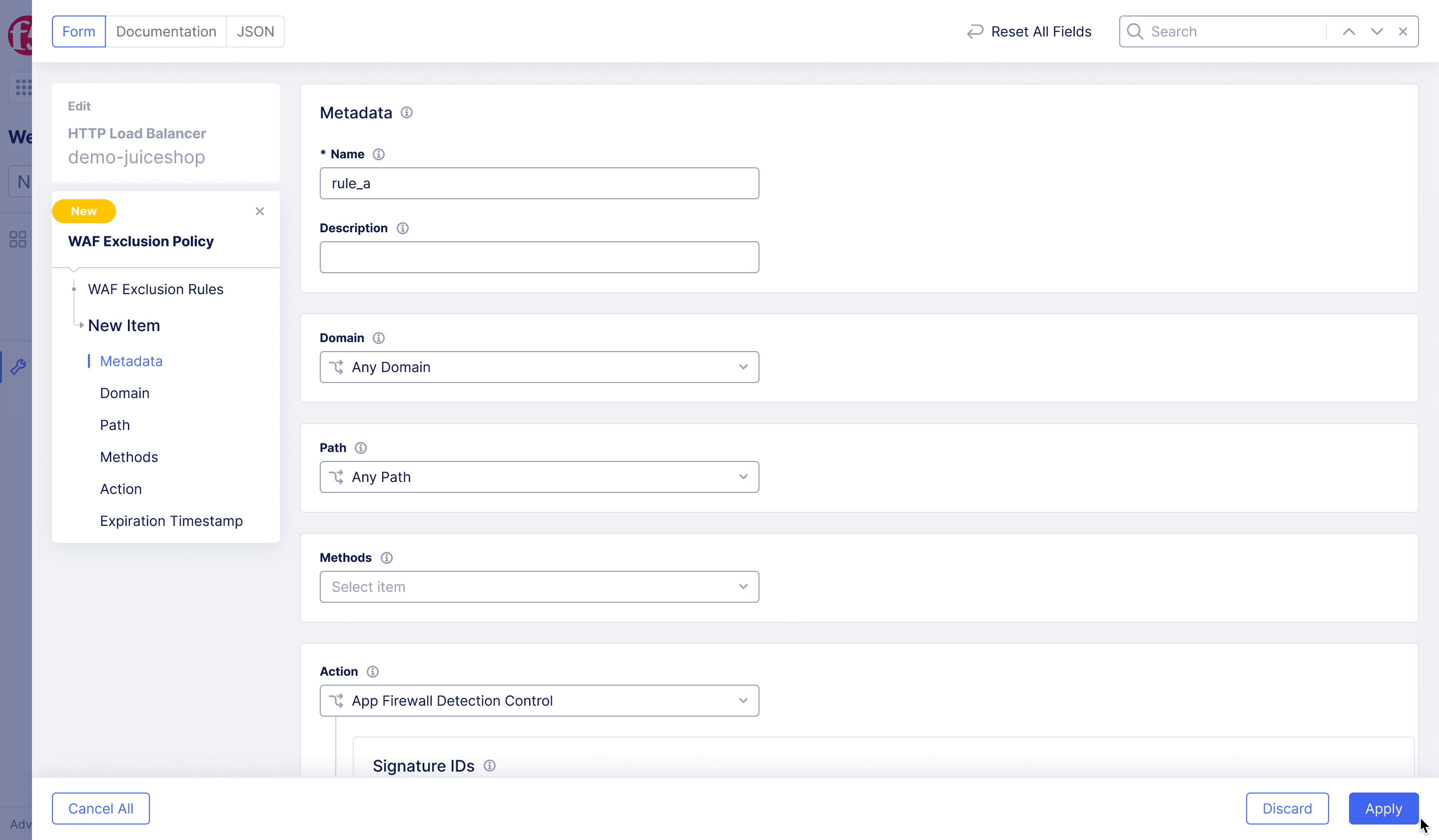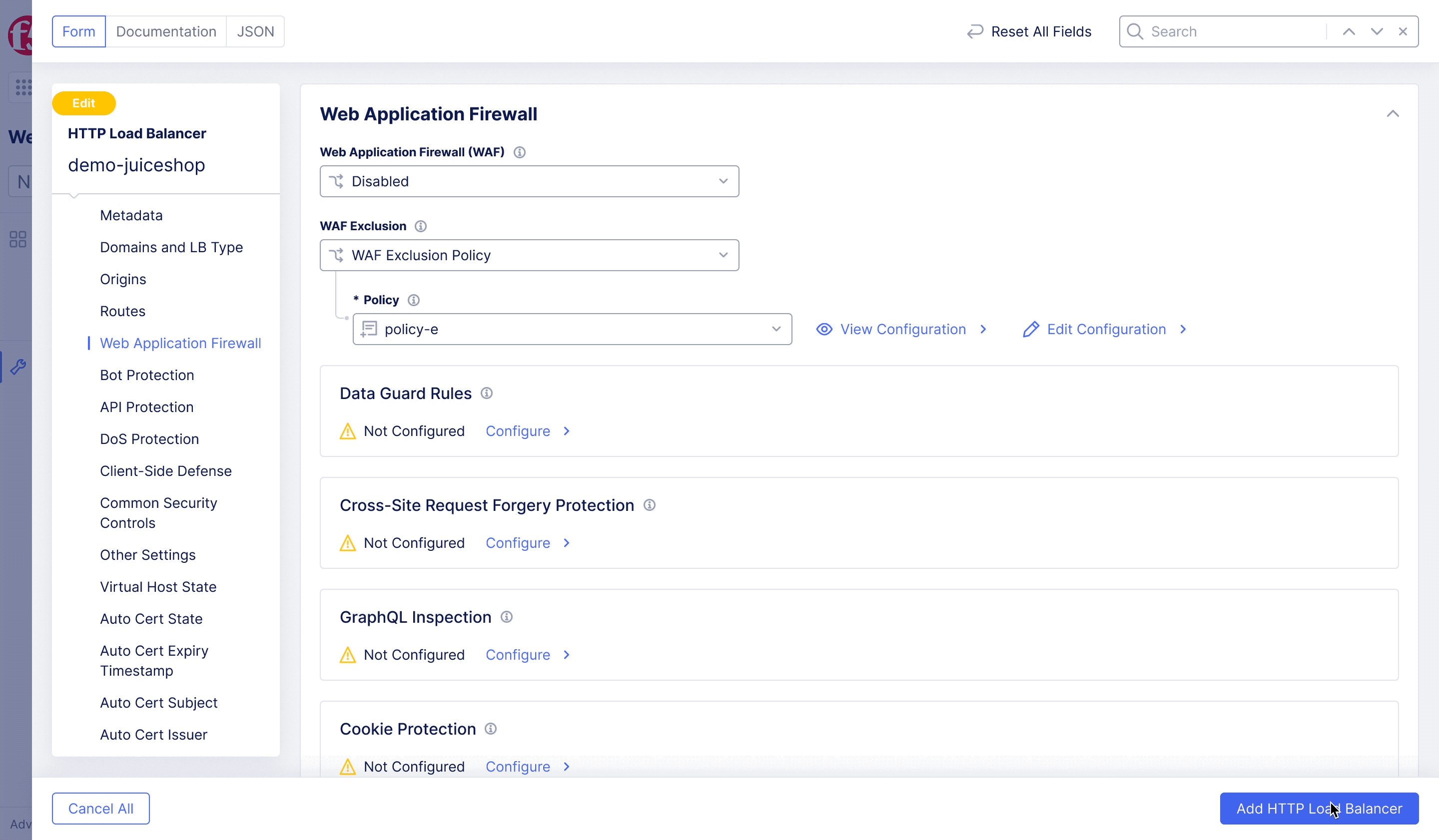
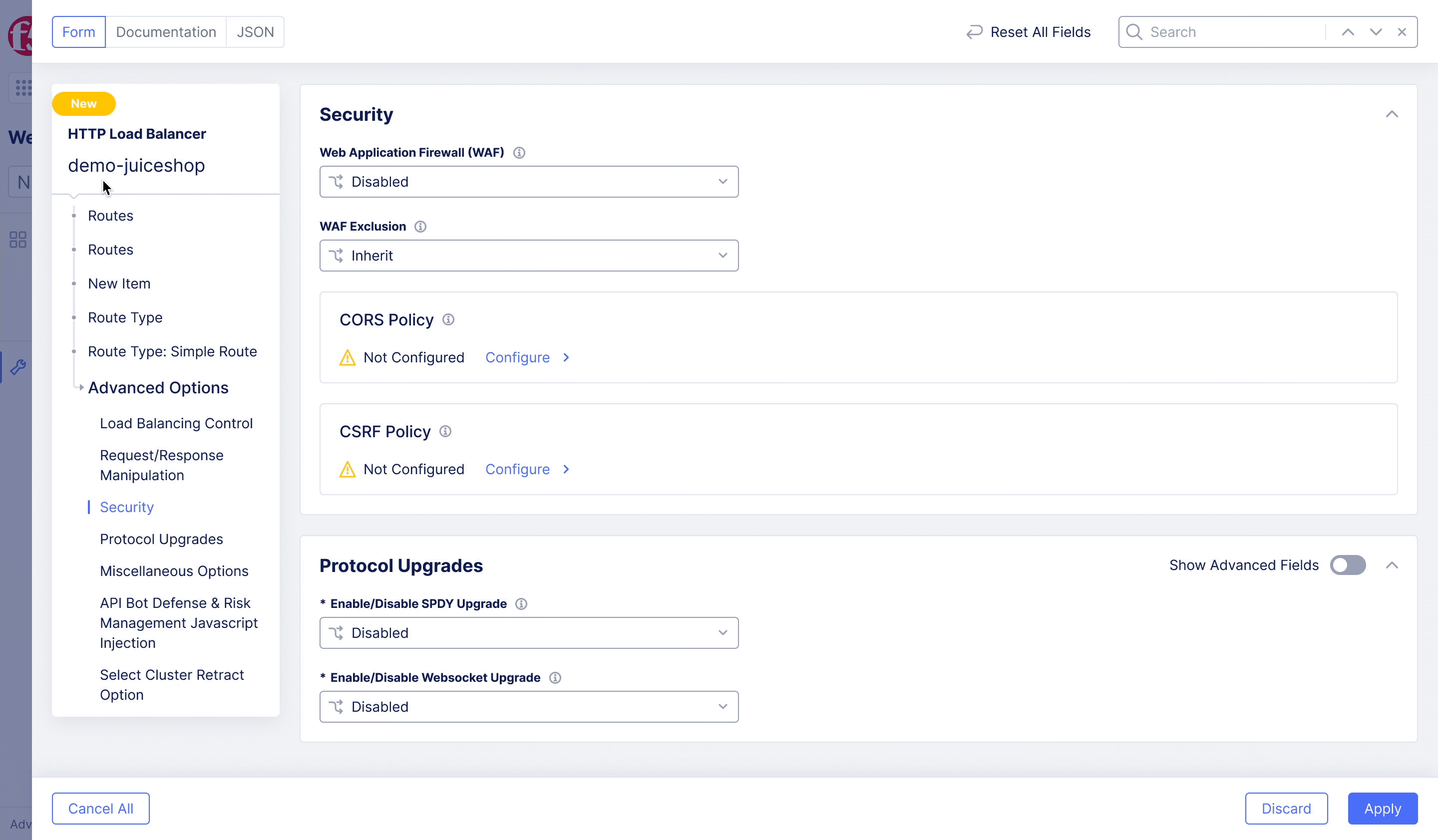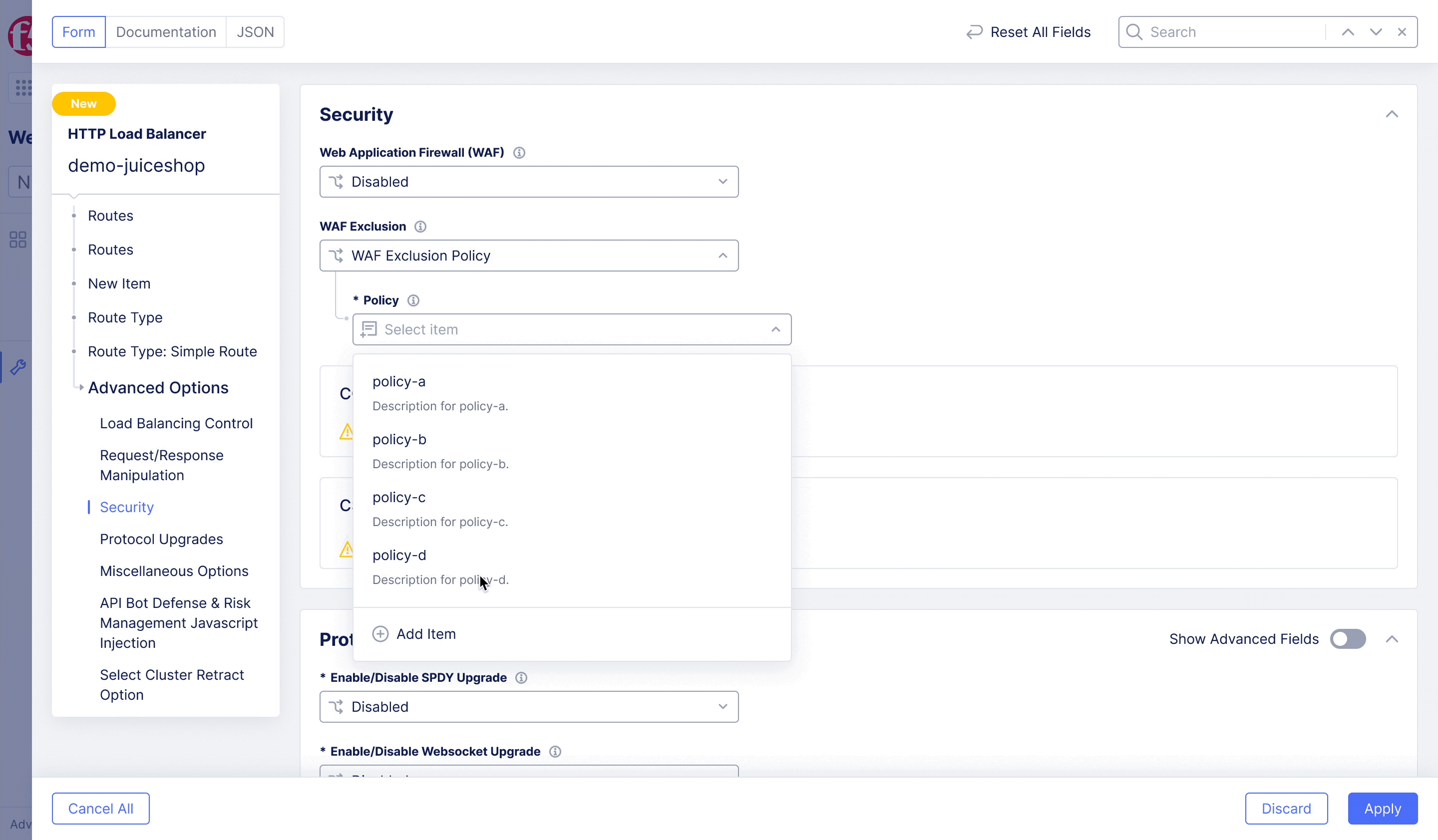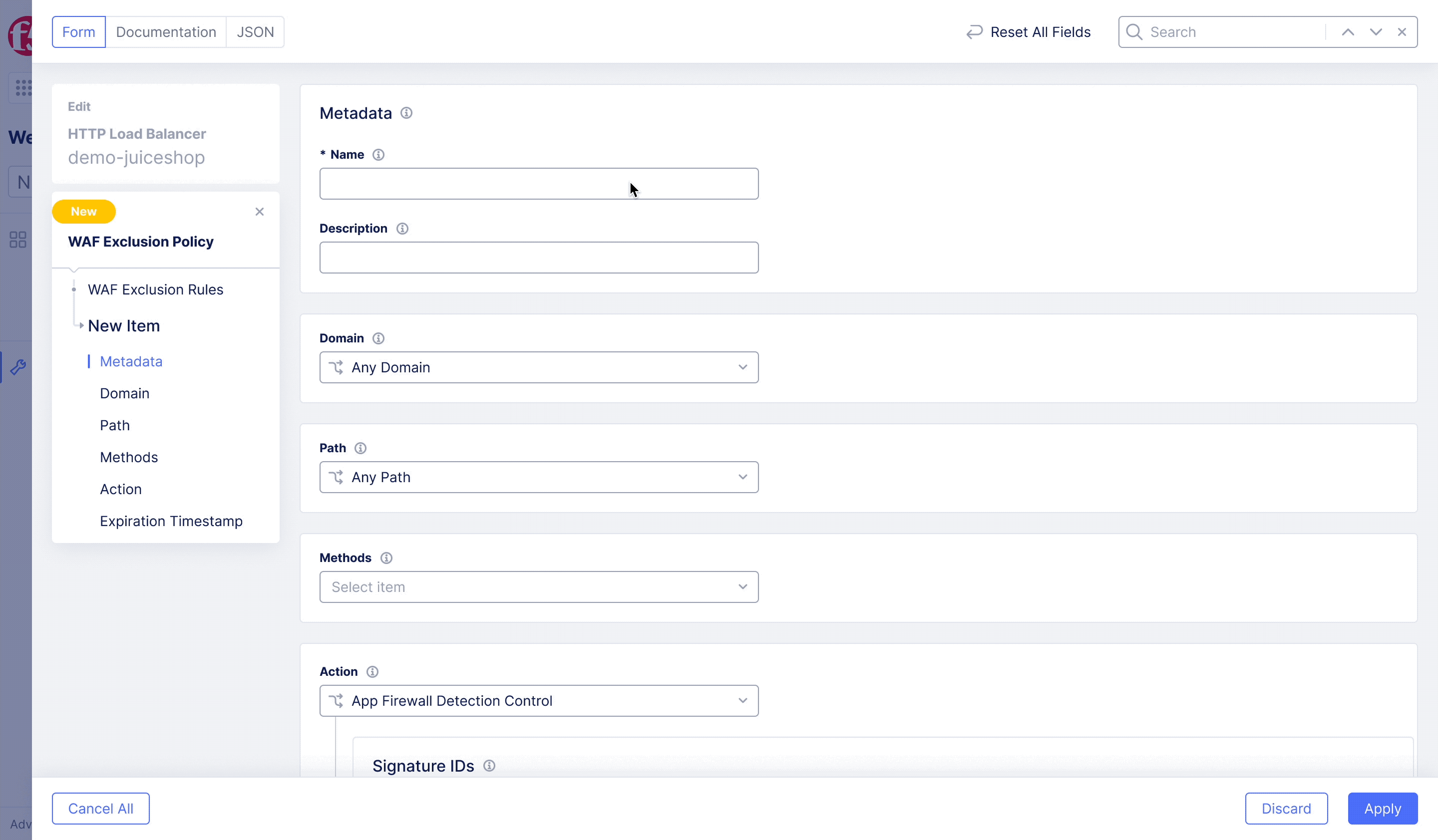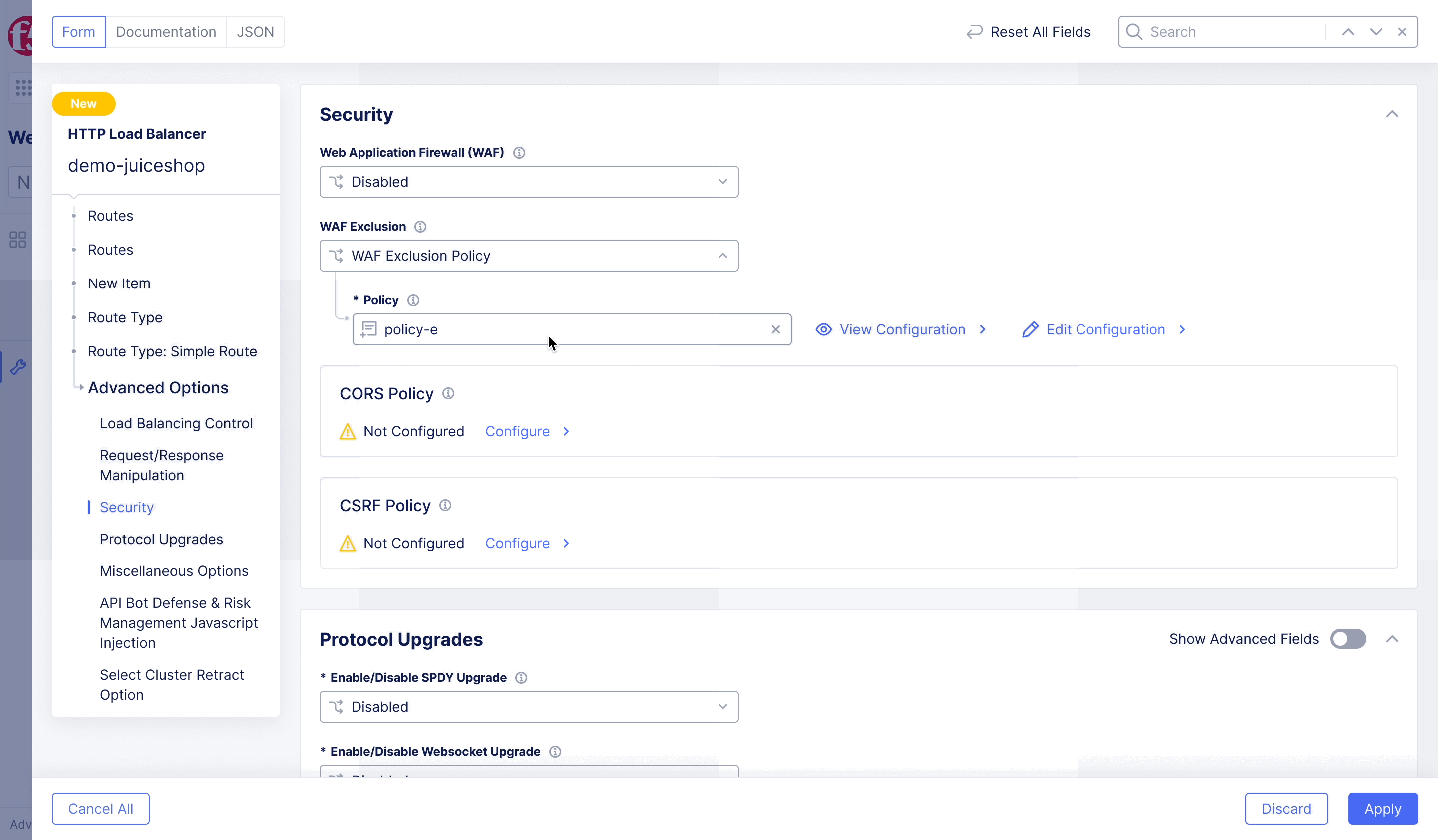
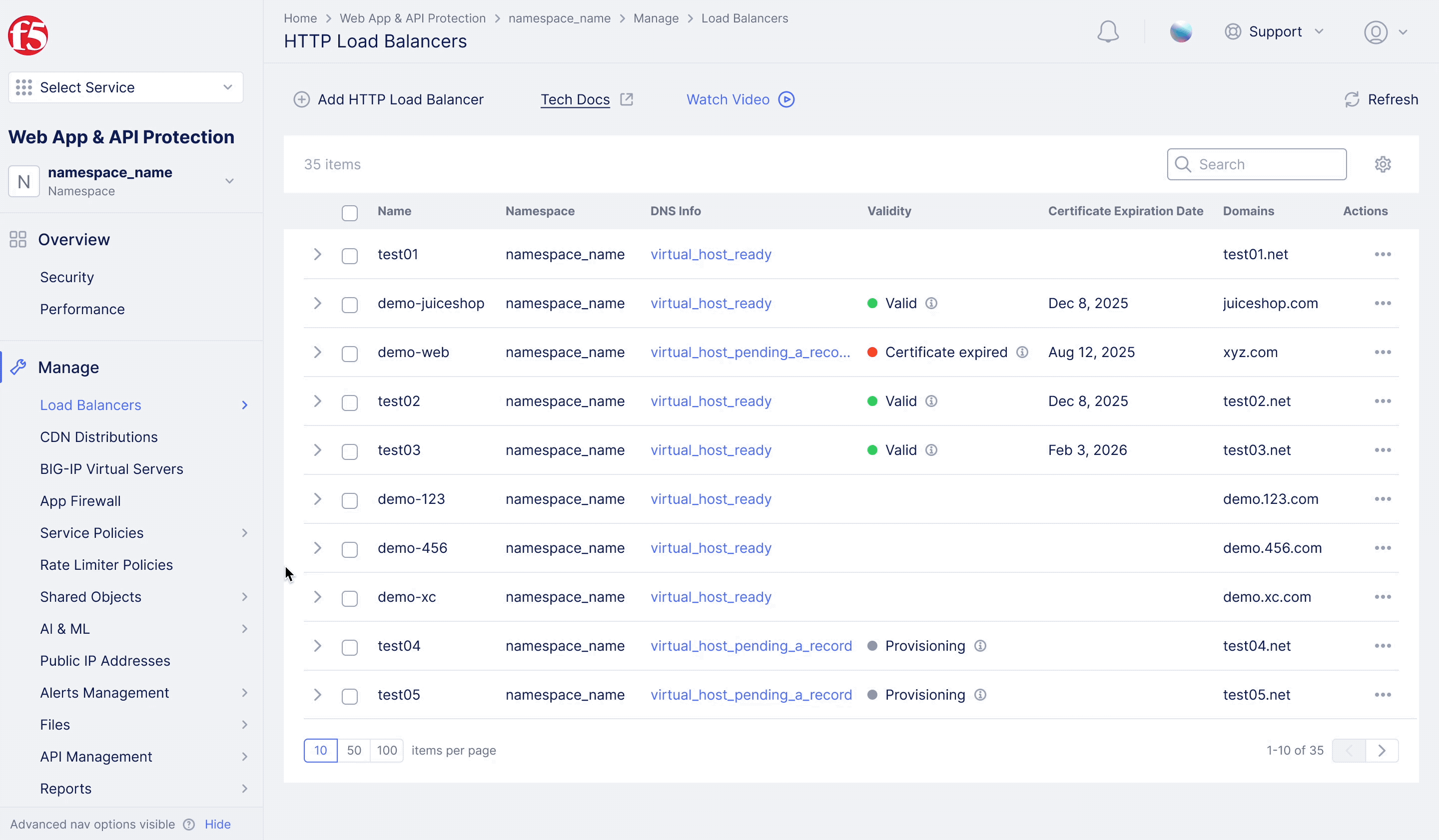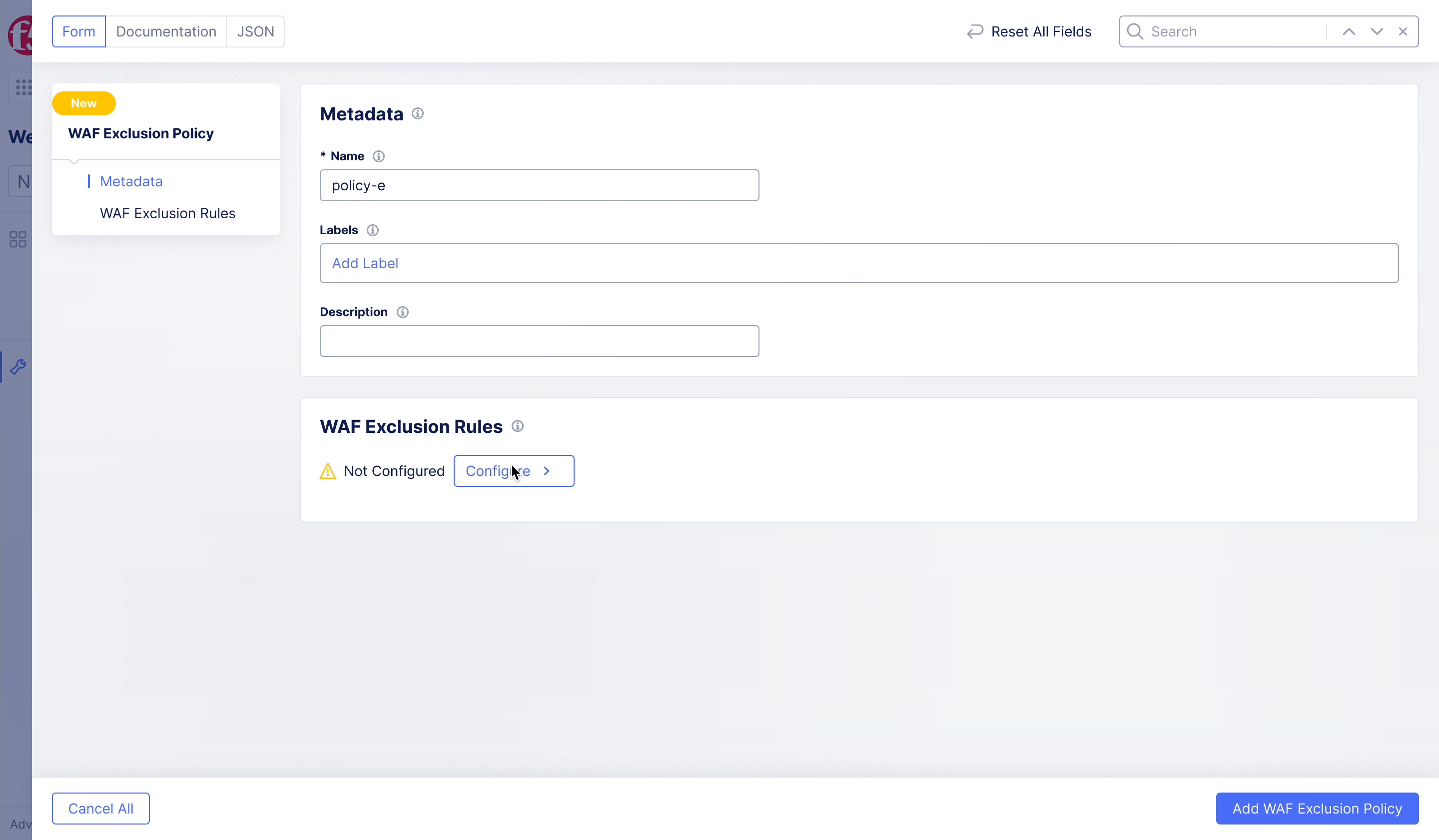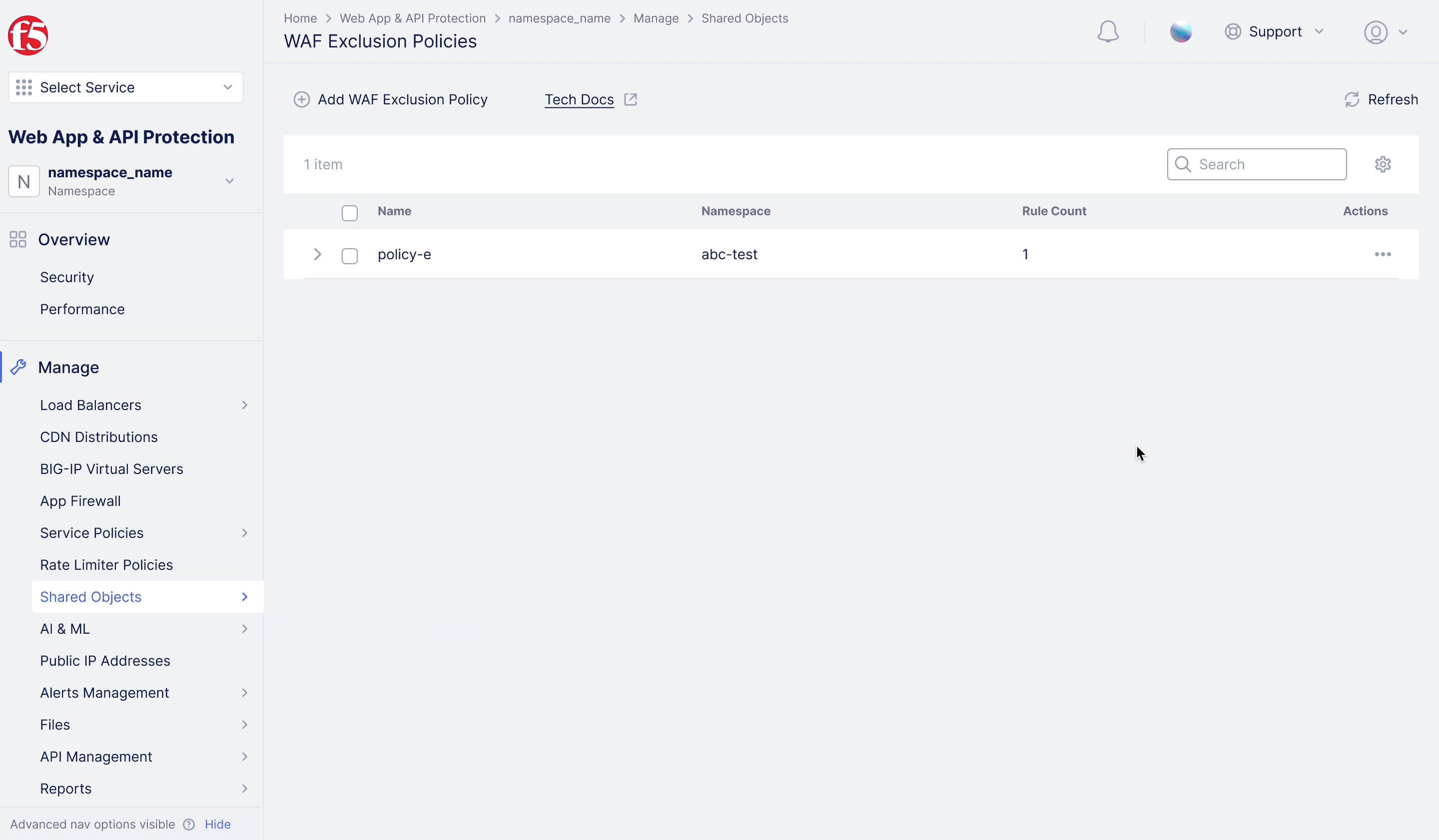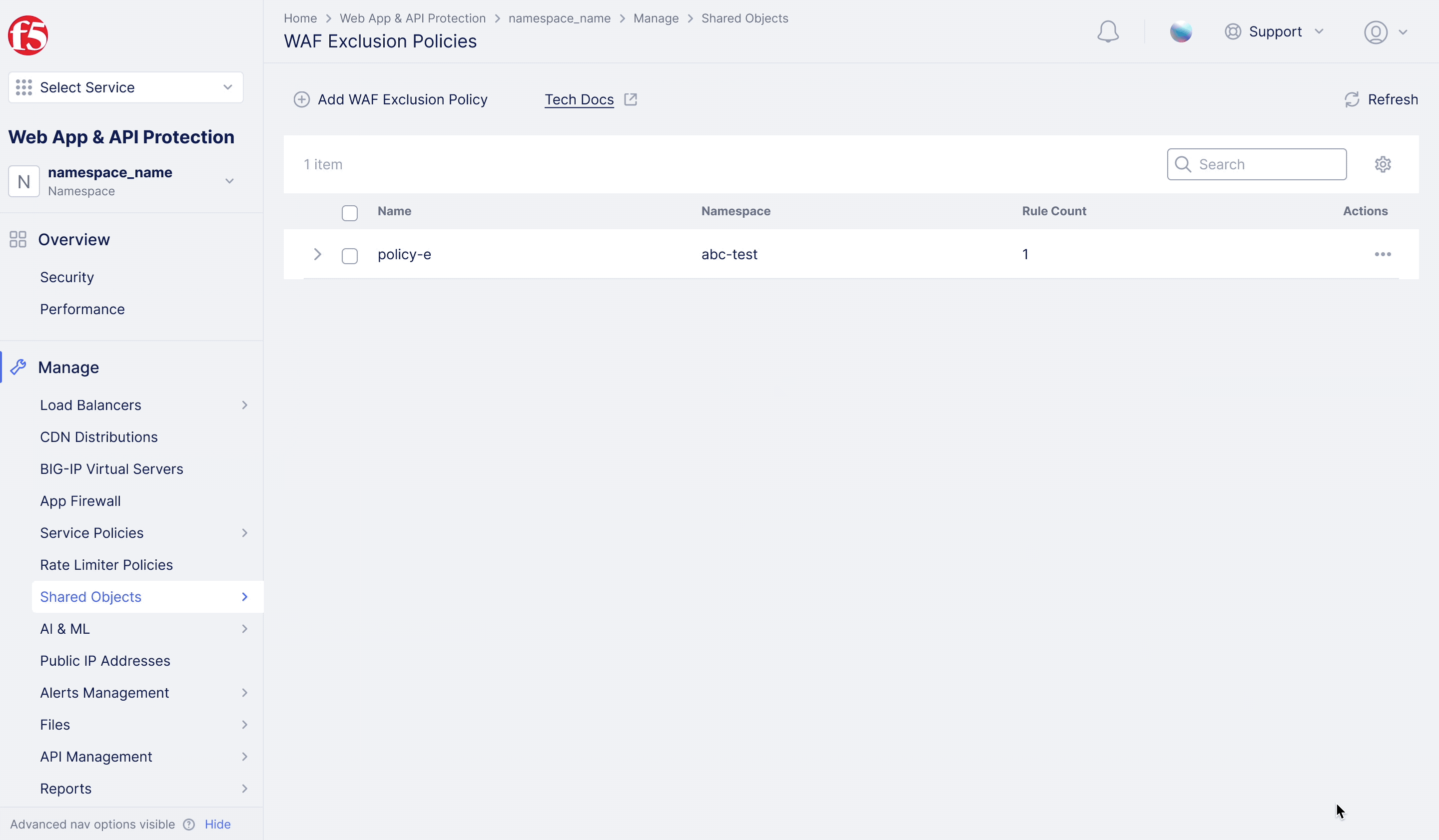
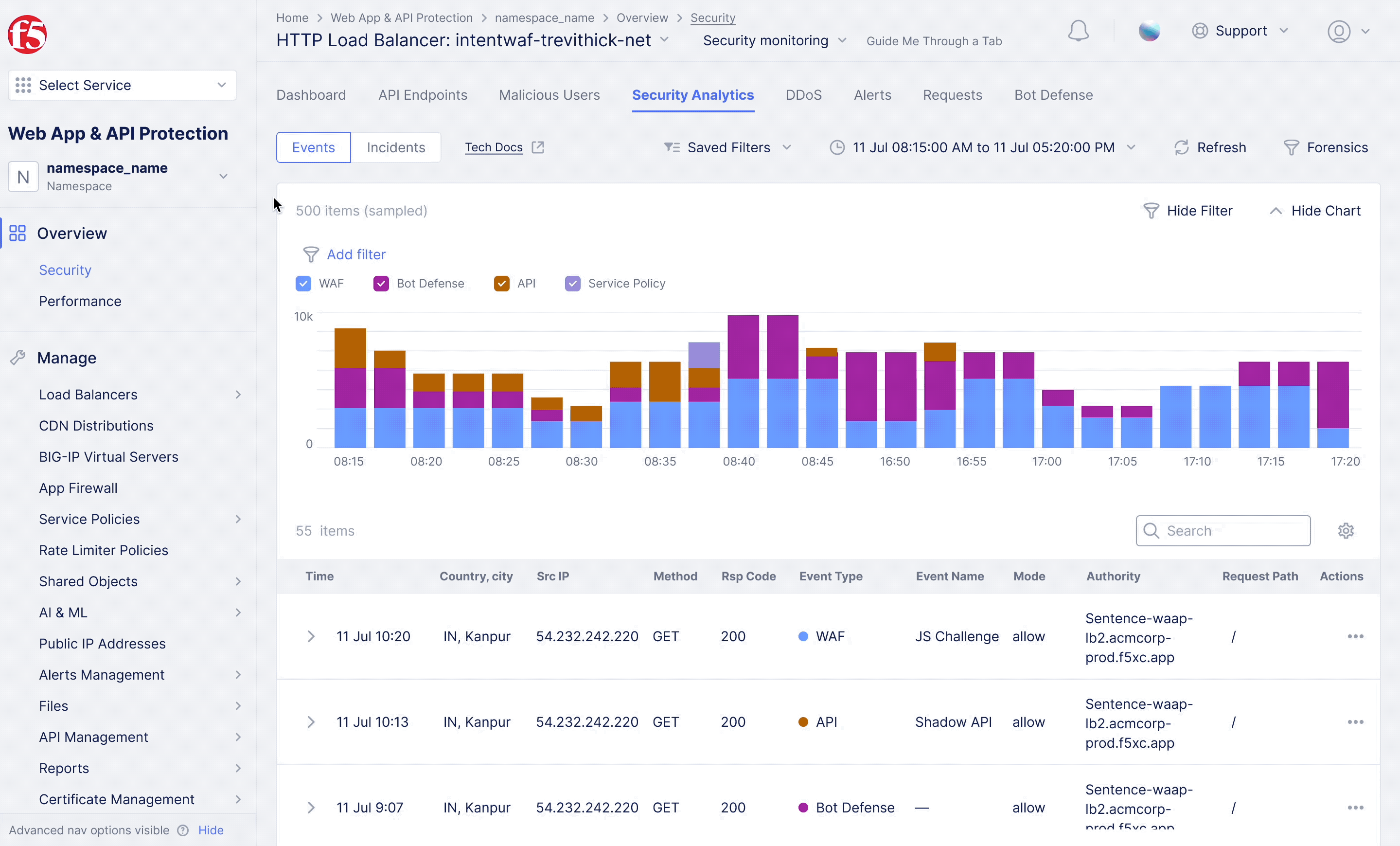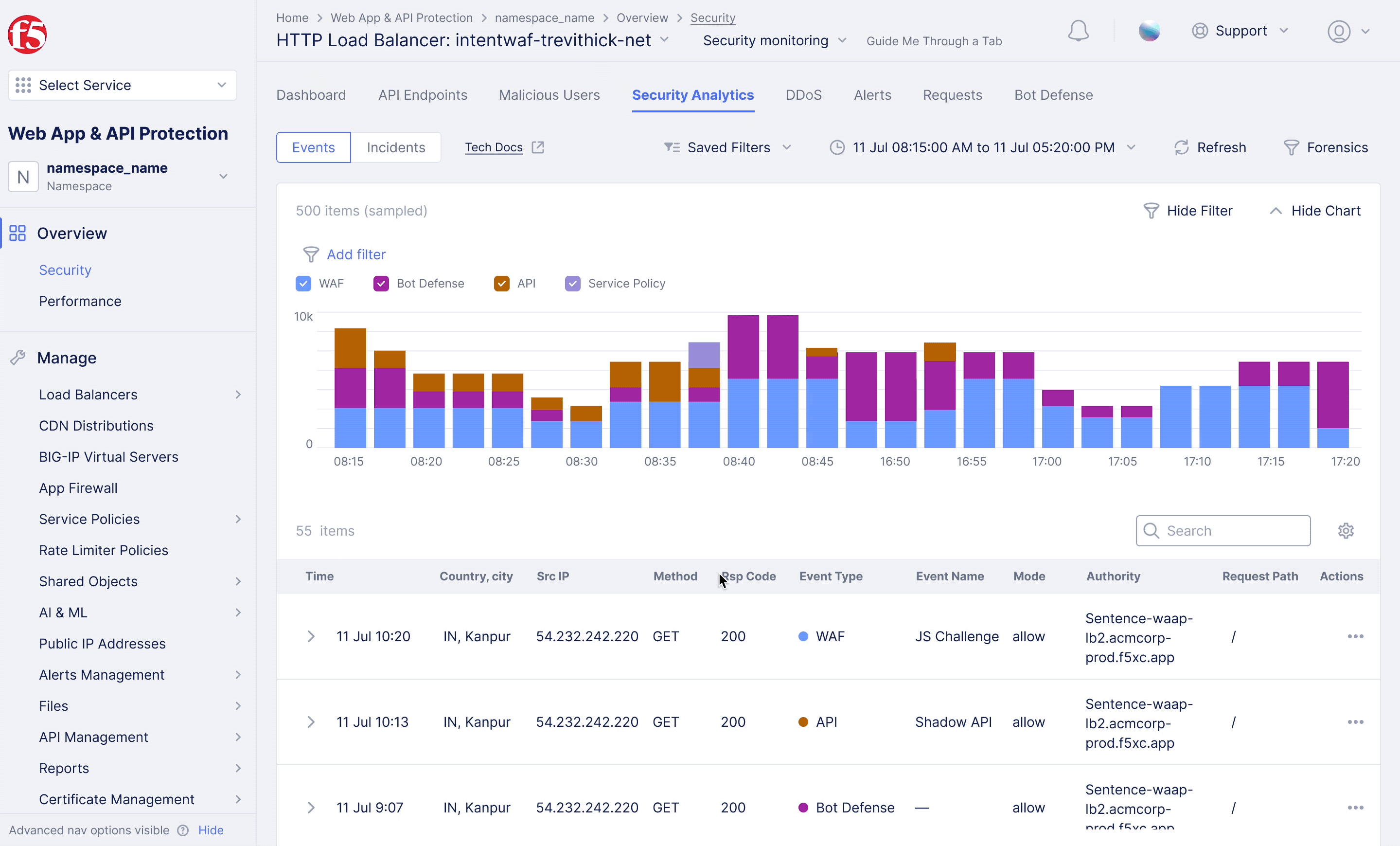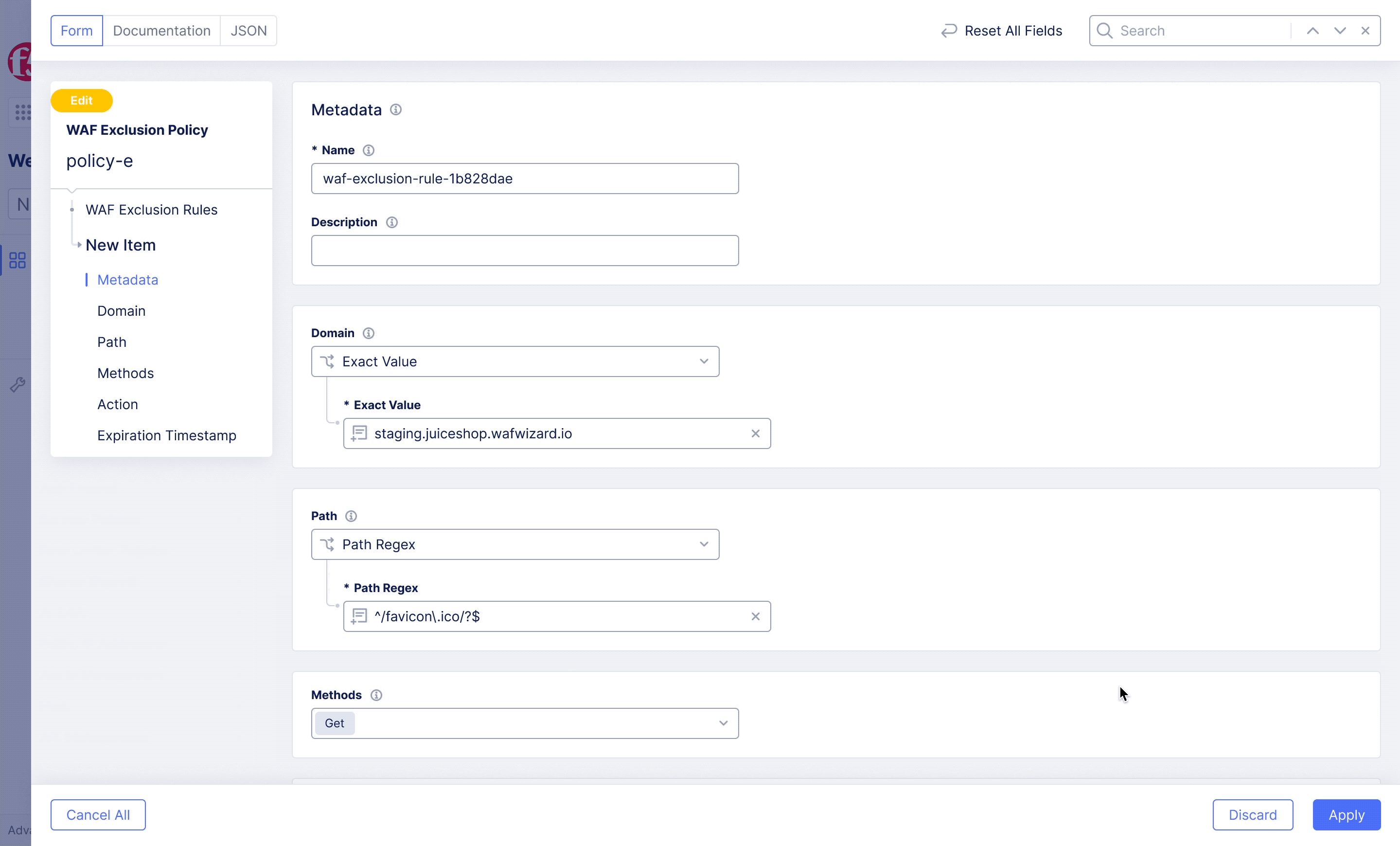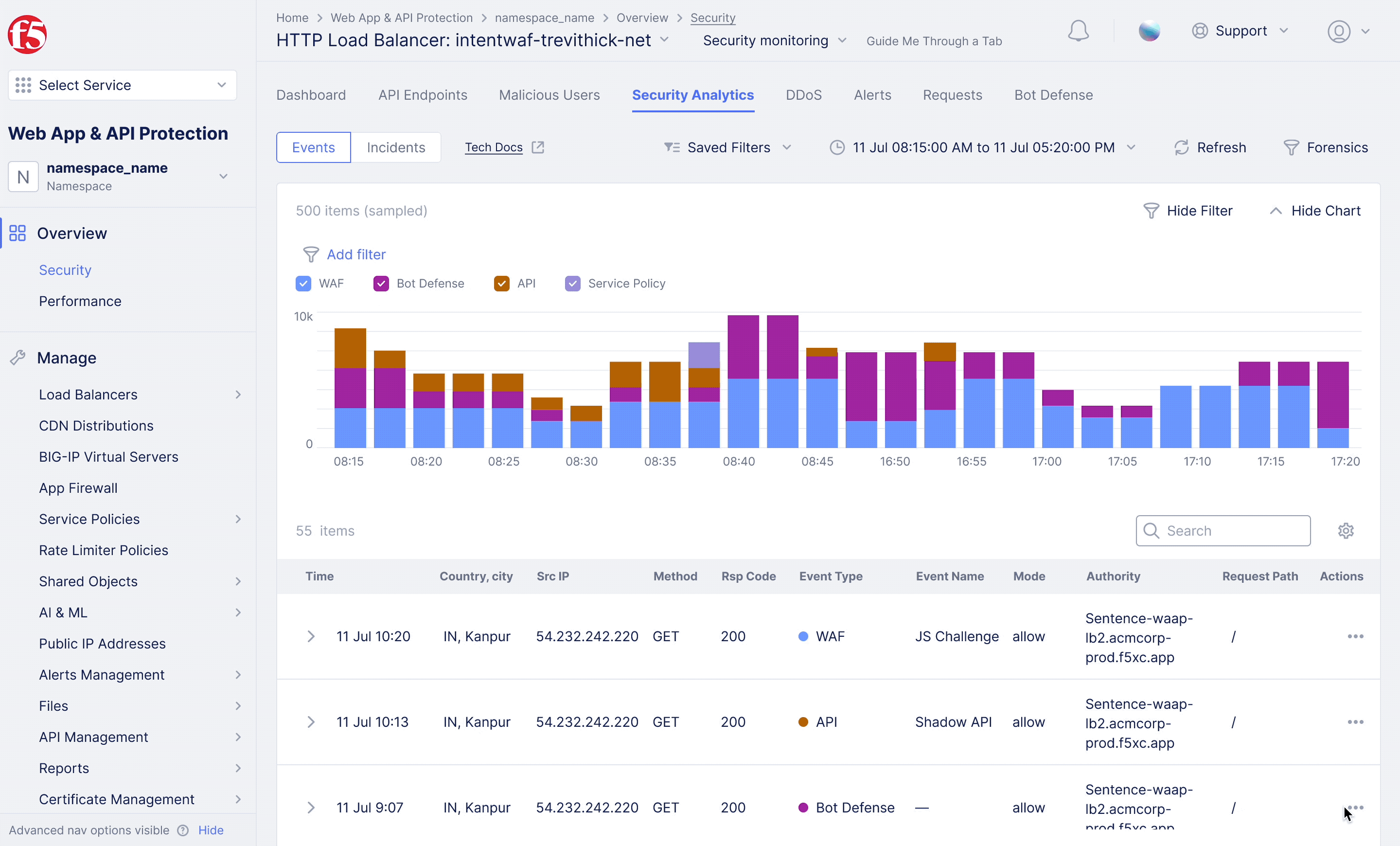
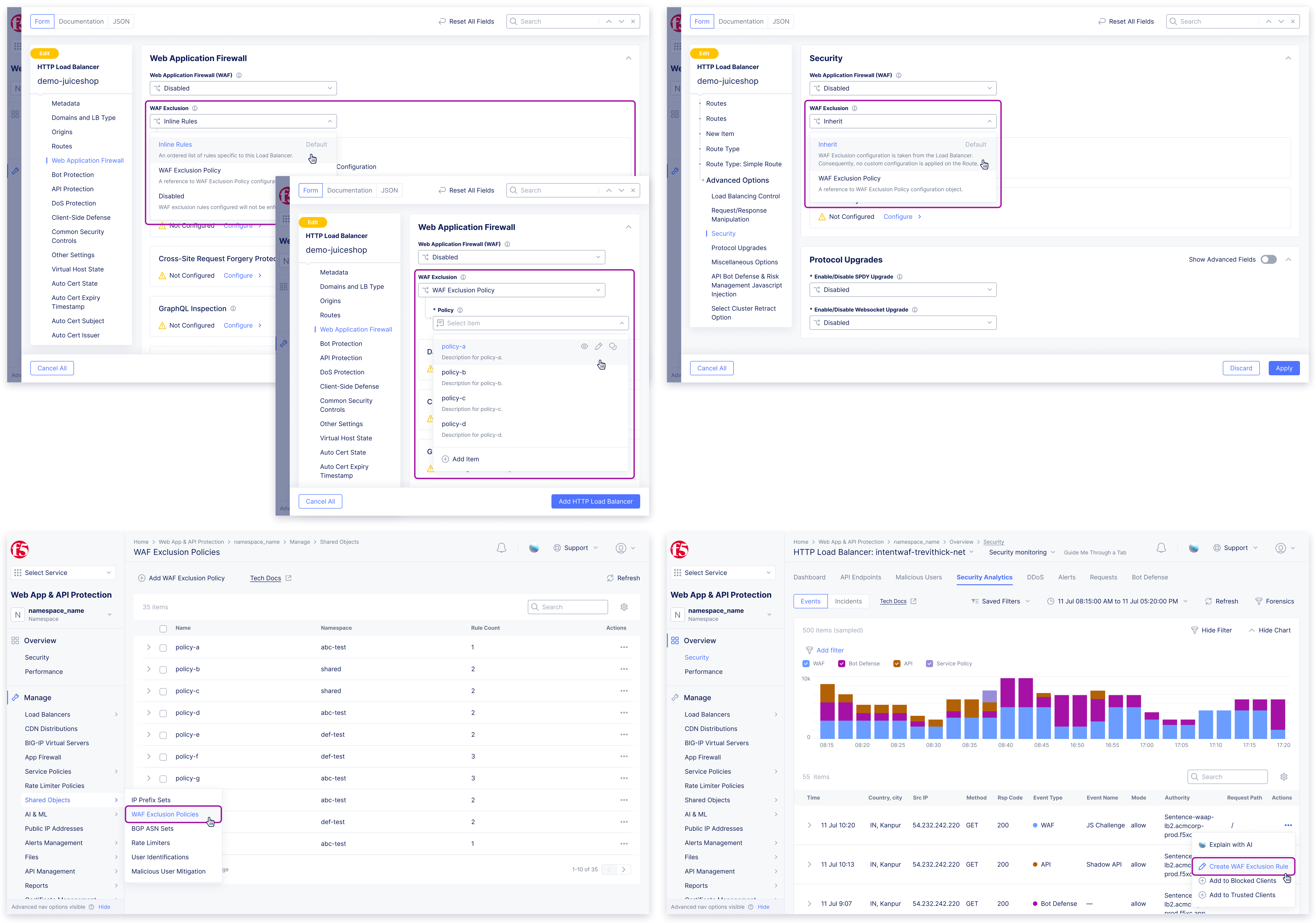
F5XC – WAF Exclusion Policy
Achieving flexible blocking and false positive prevention.
Project Type: |
UX Designer at F5 |
Duration: |
Nov. 2024 – Feb. 2025 |
Members: |
2 designers, 5 developers, 1 PM |
Practice Areas: |
UX design, information architecture, interaction design |
My Role: |
I served as a UX design lead and co-worked closely with PM, design system (DS) team, and both front-end and back-end developers. |