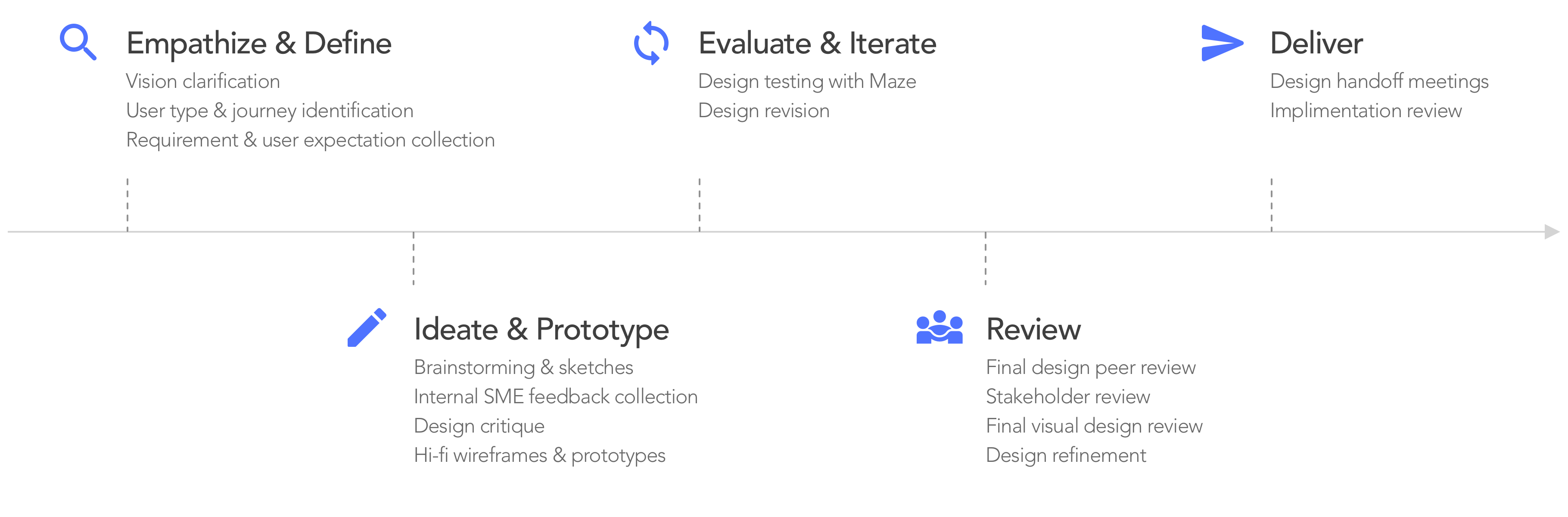
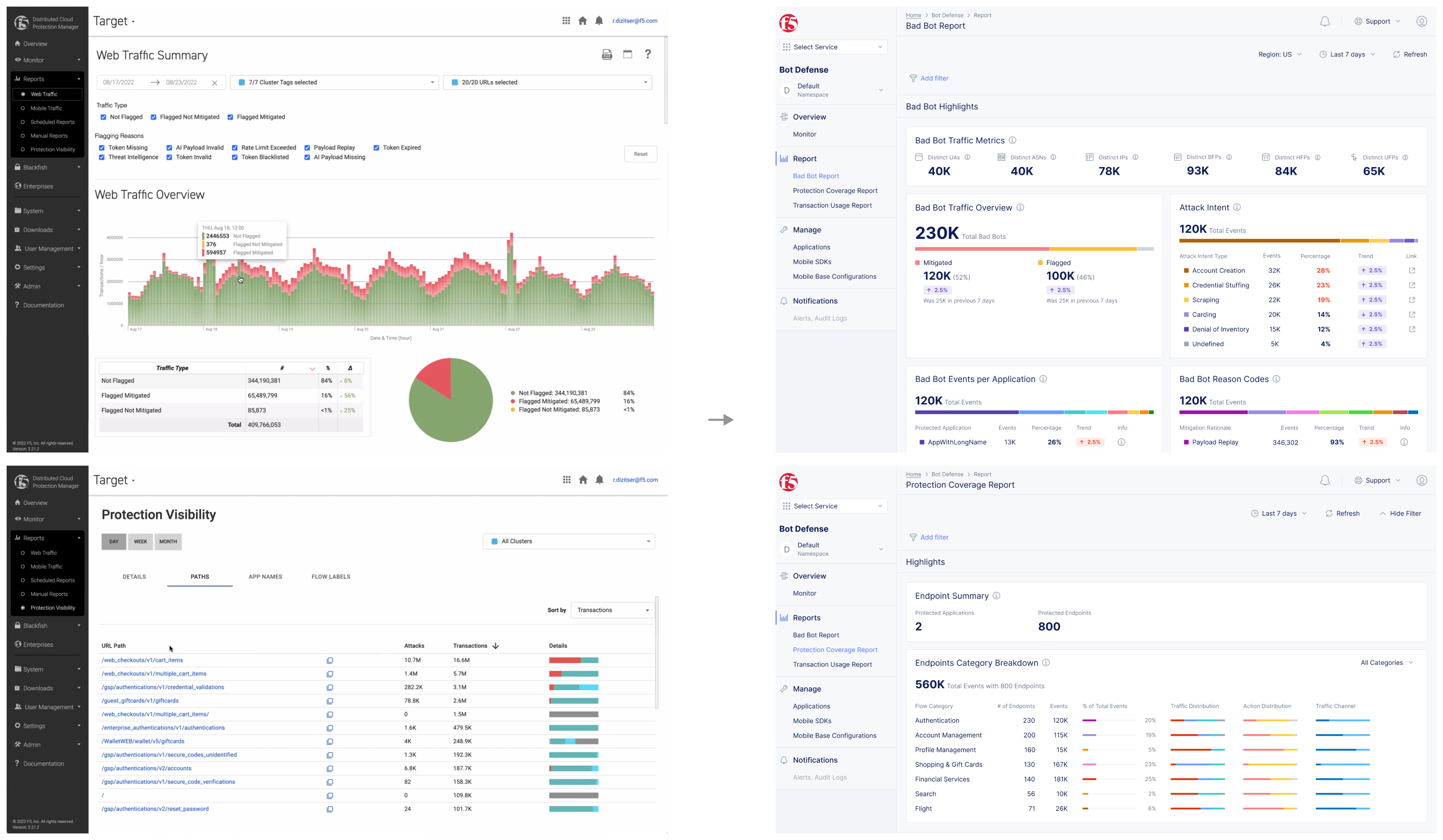
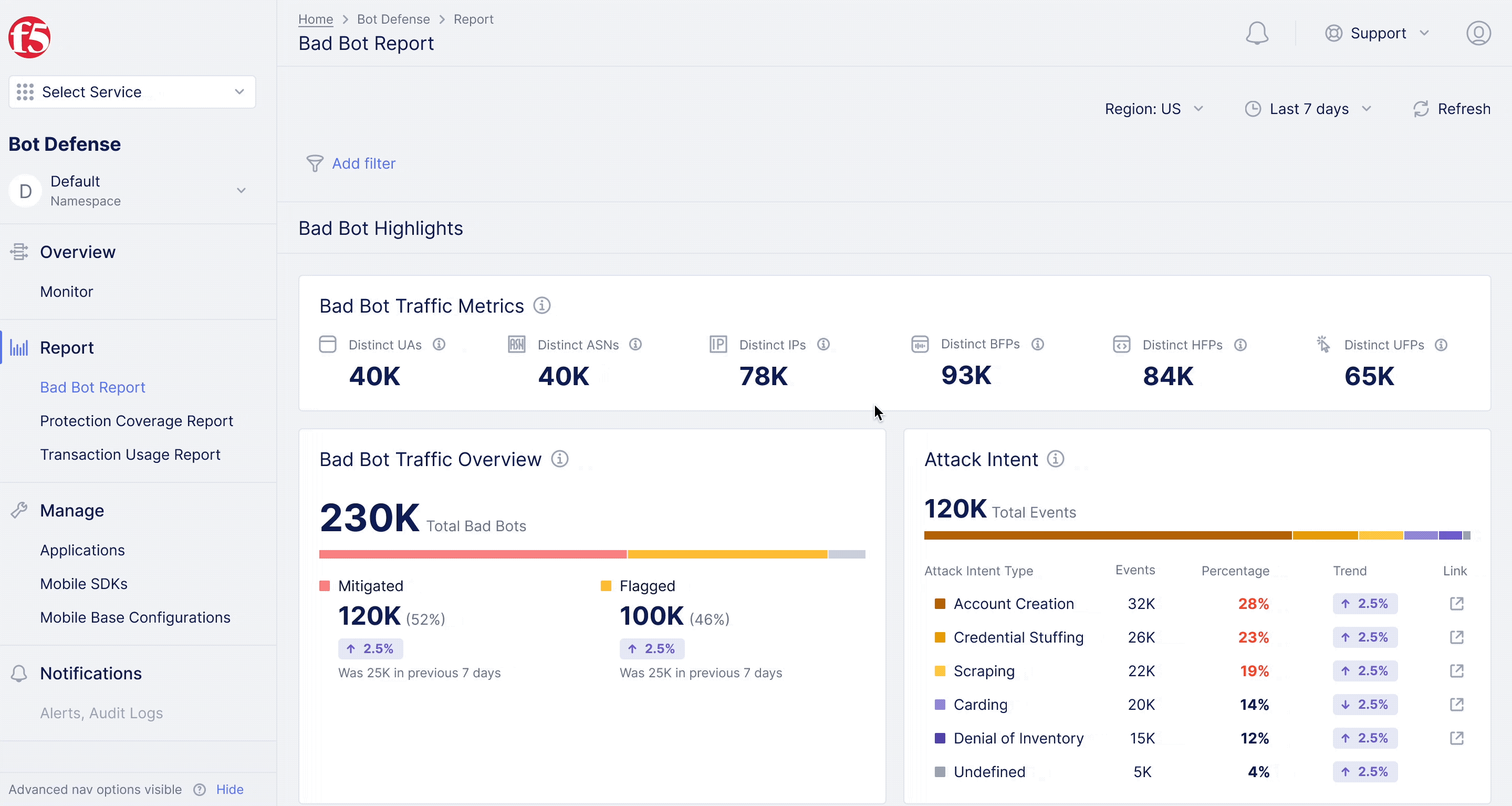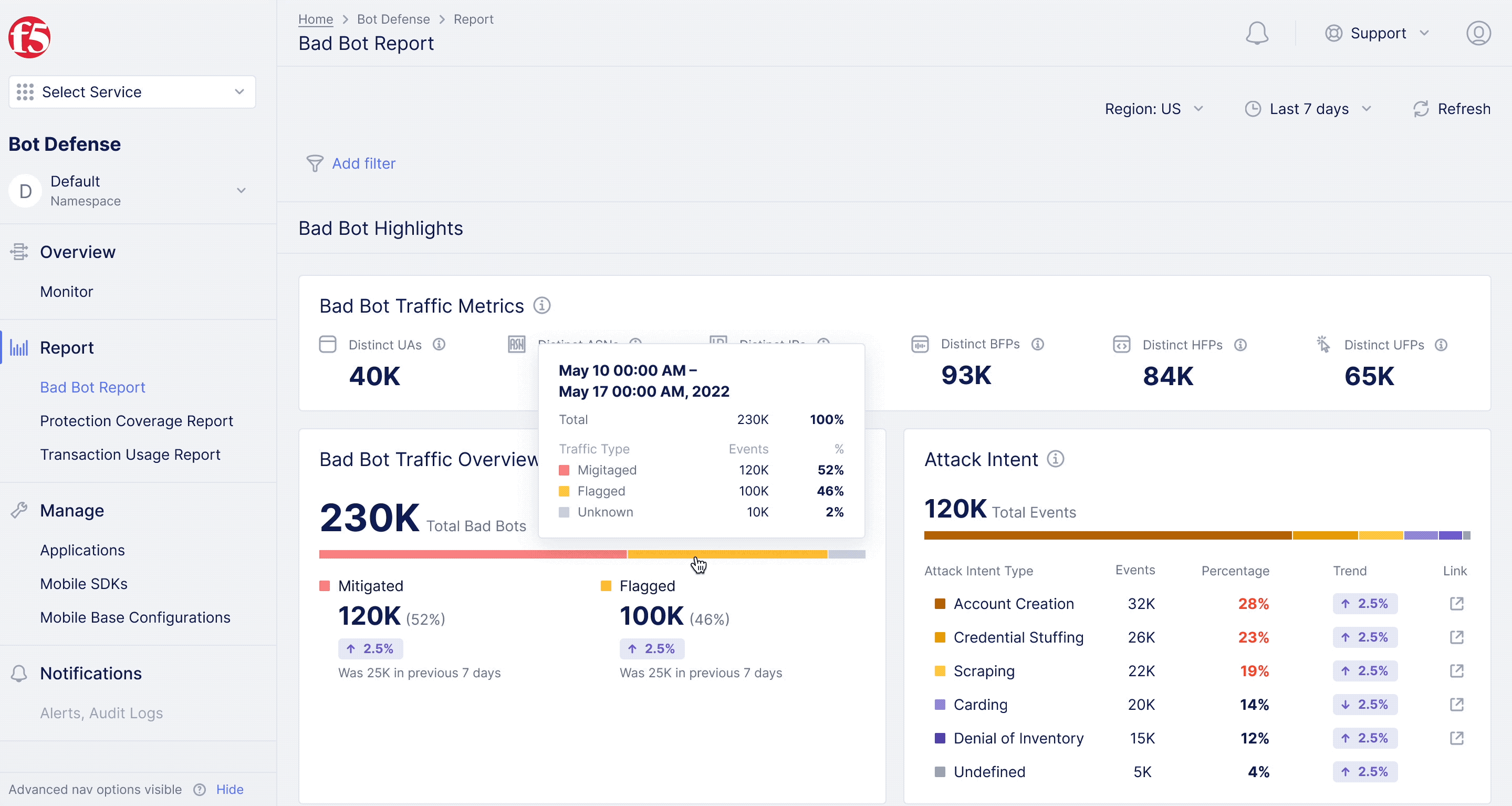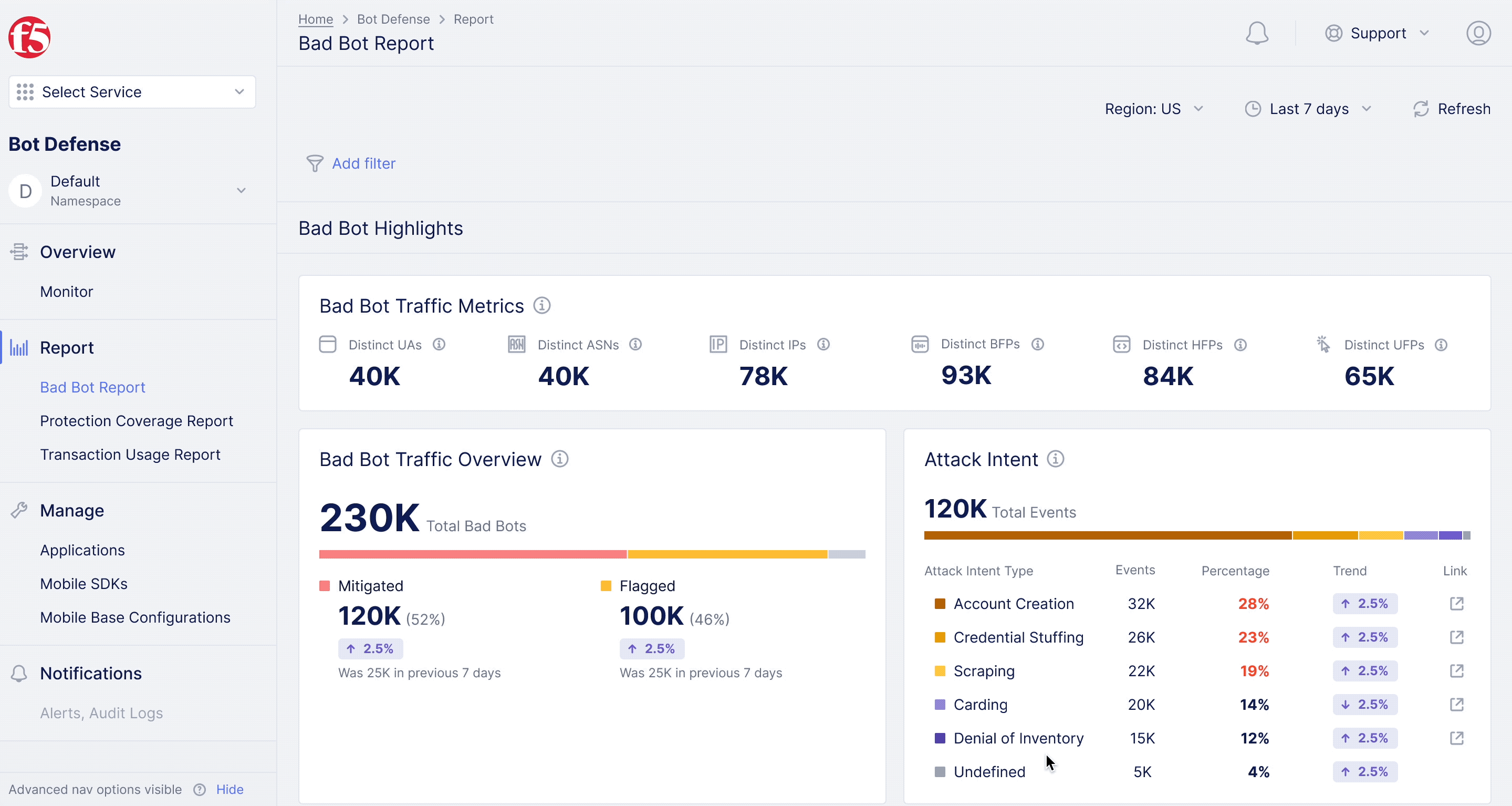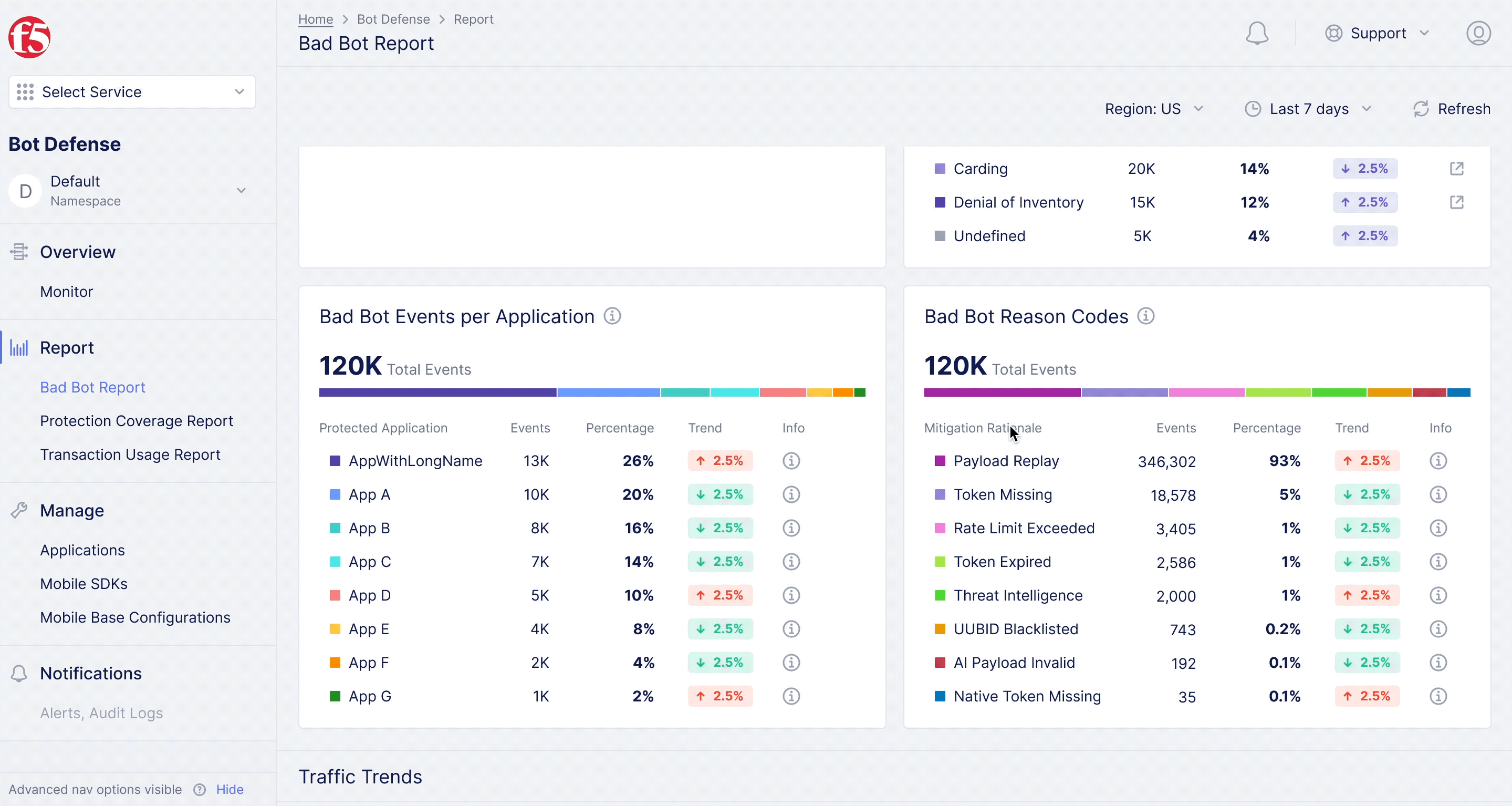
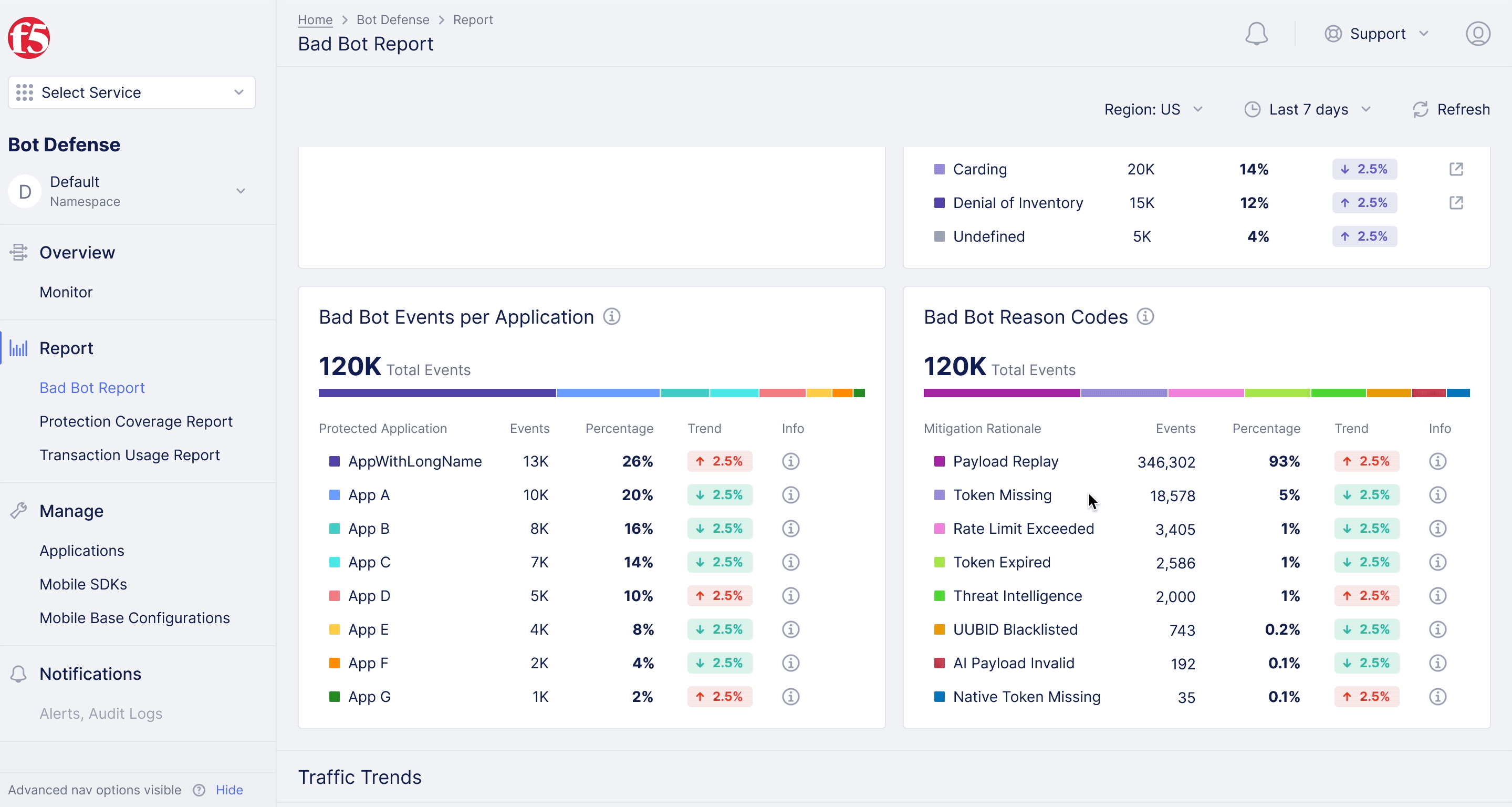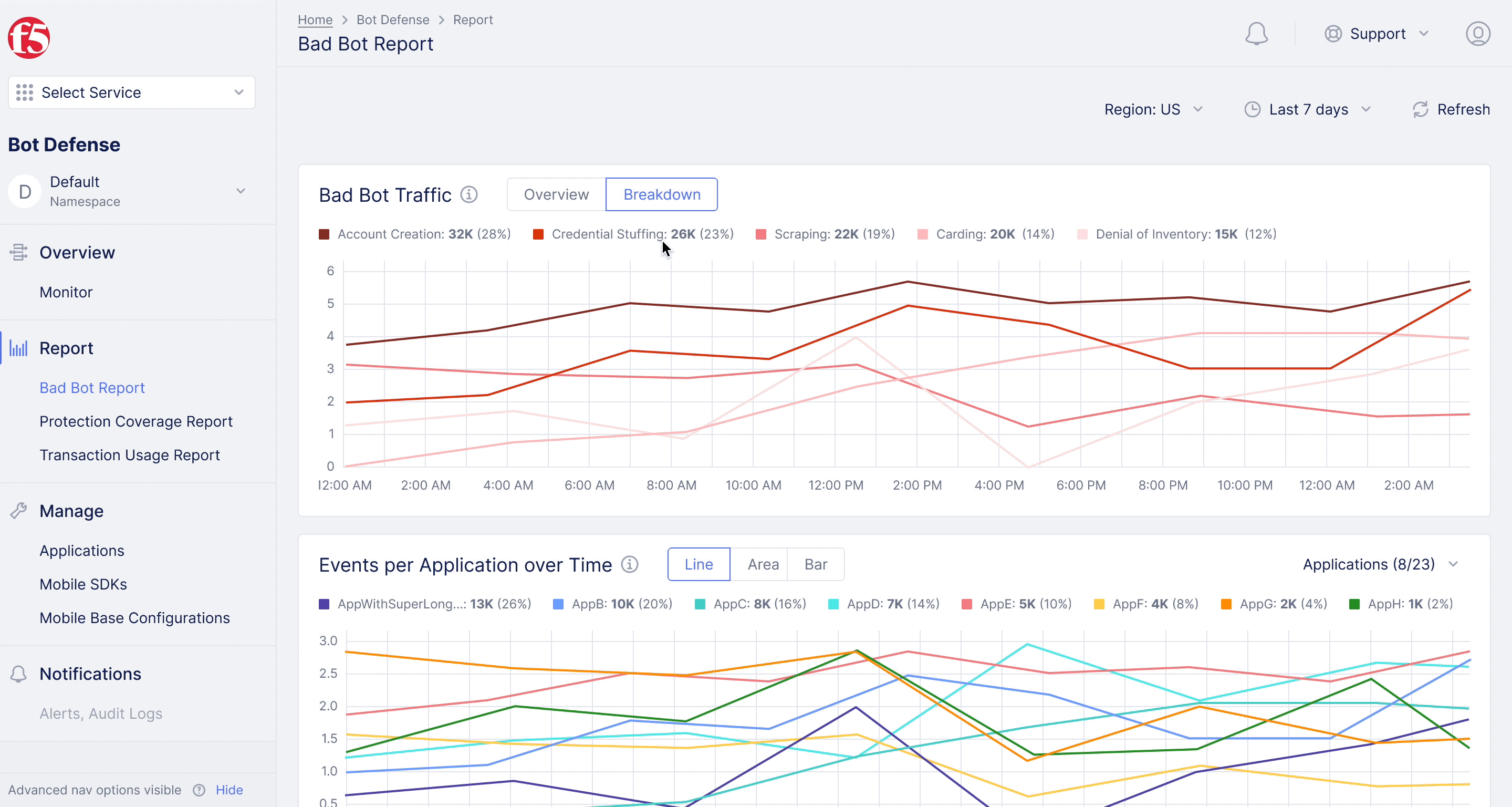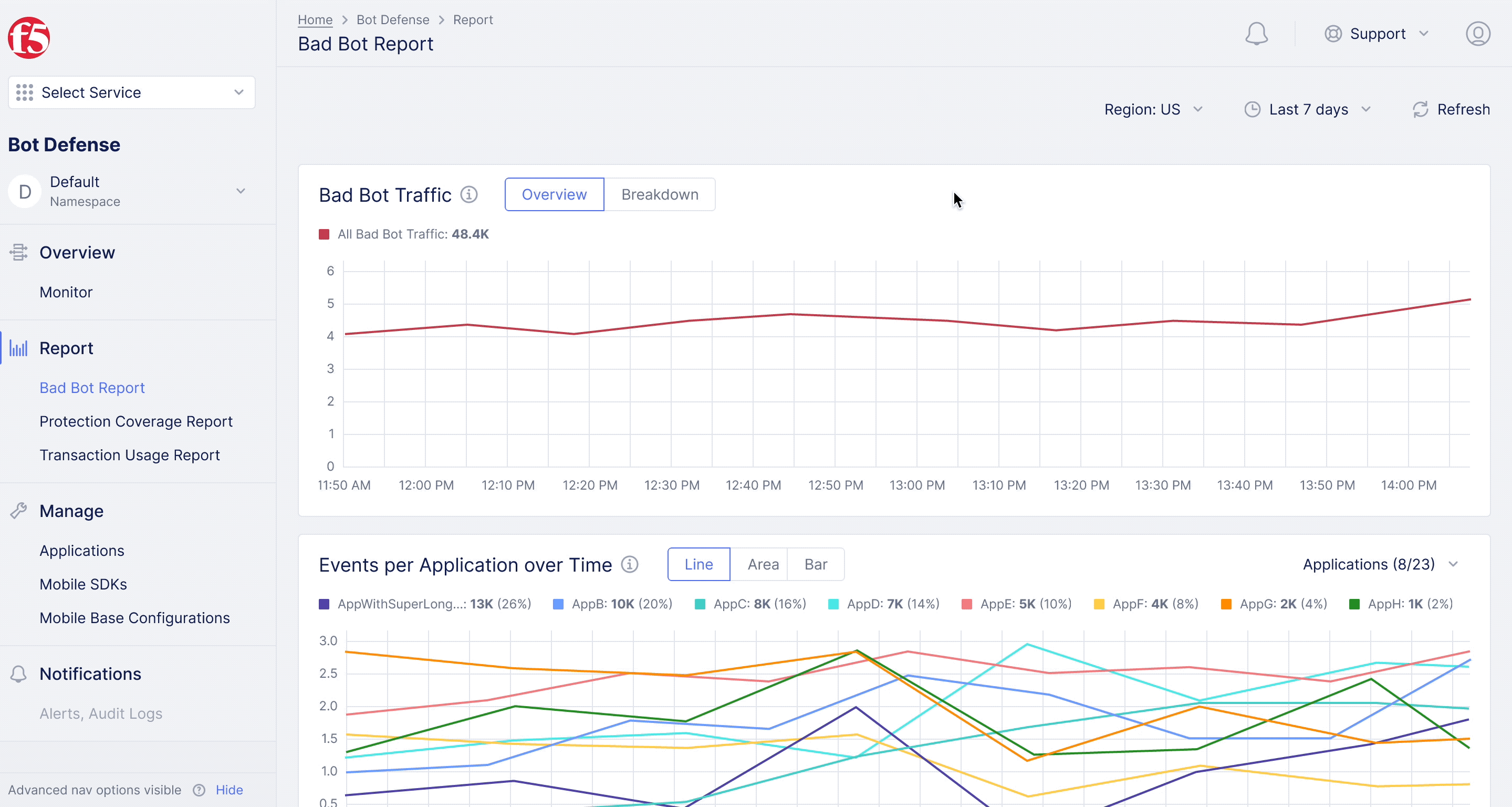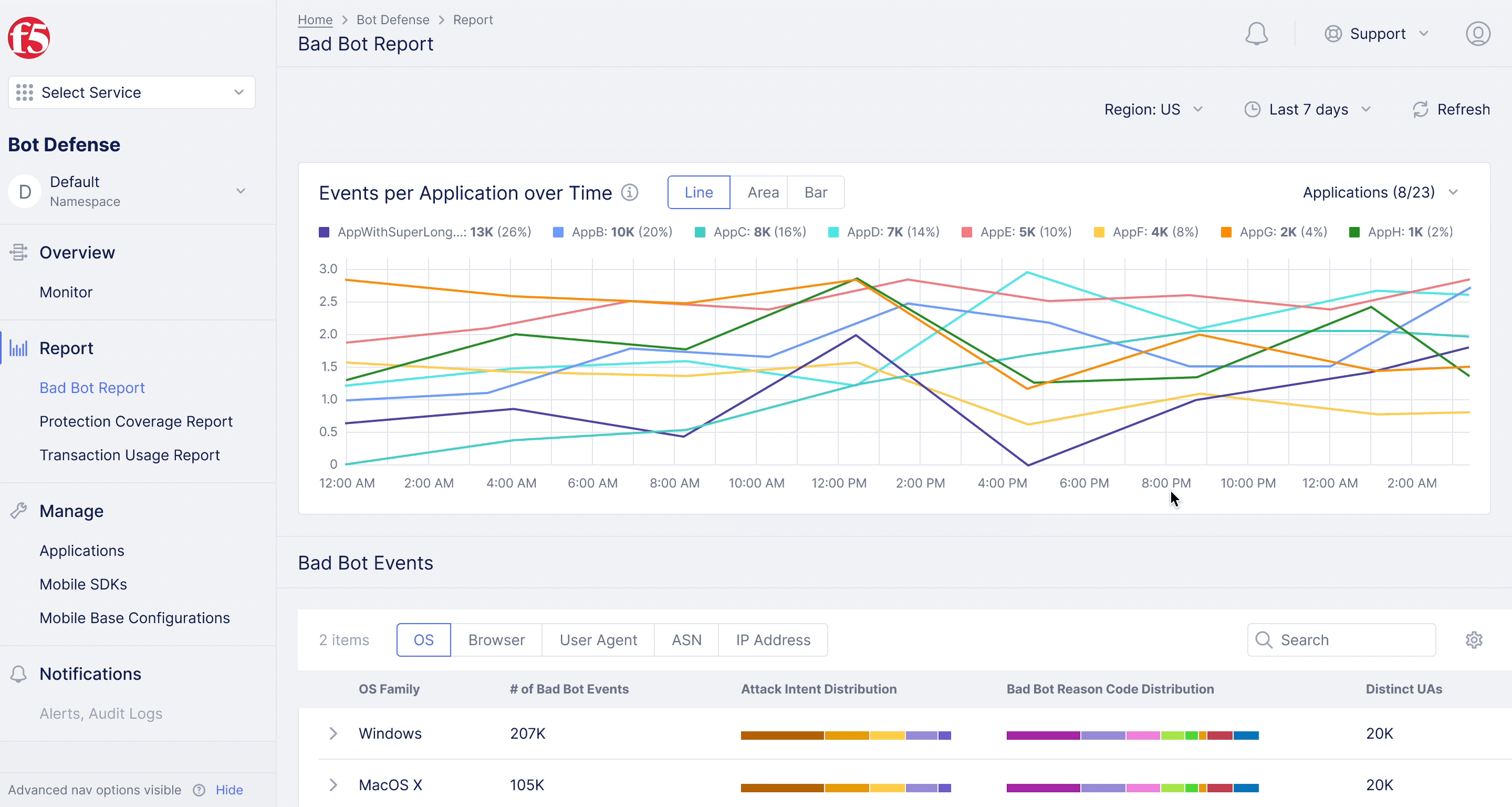
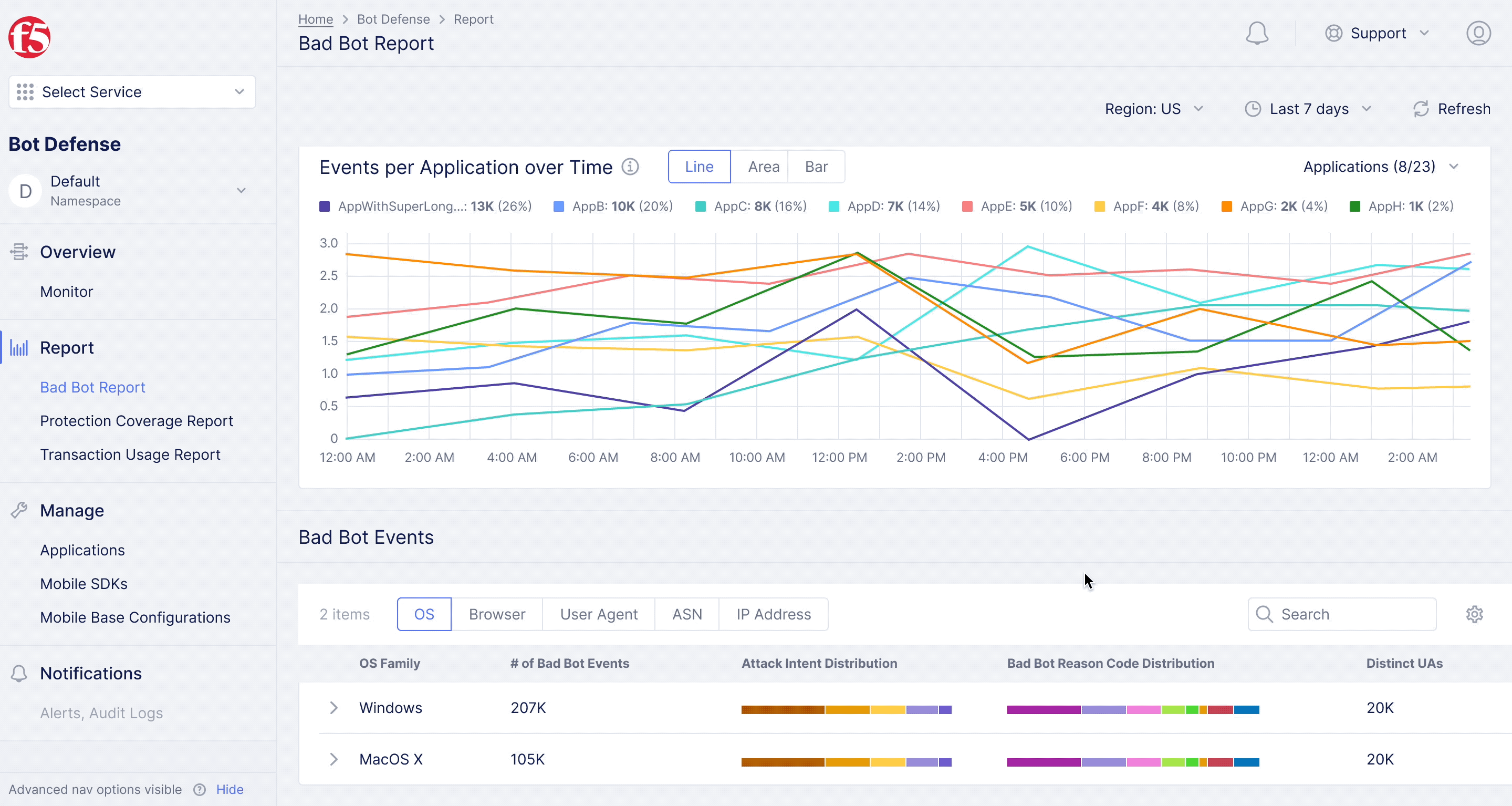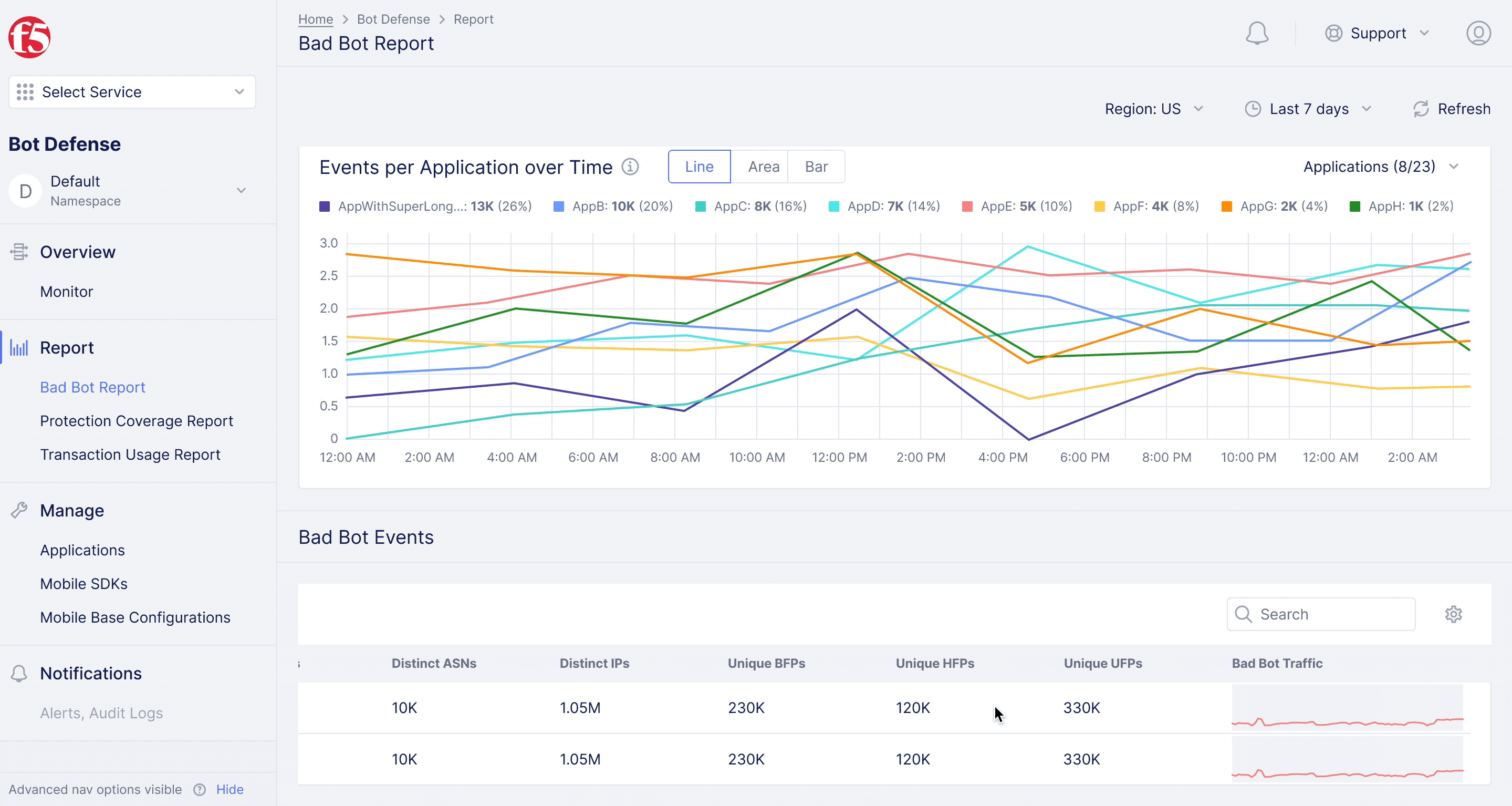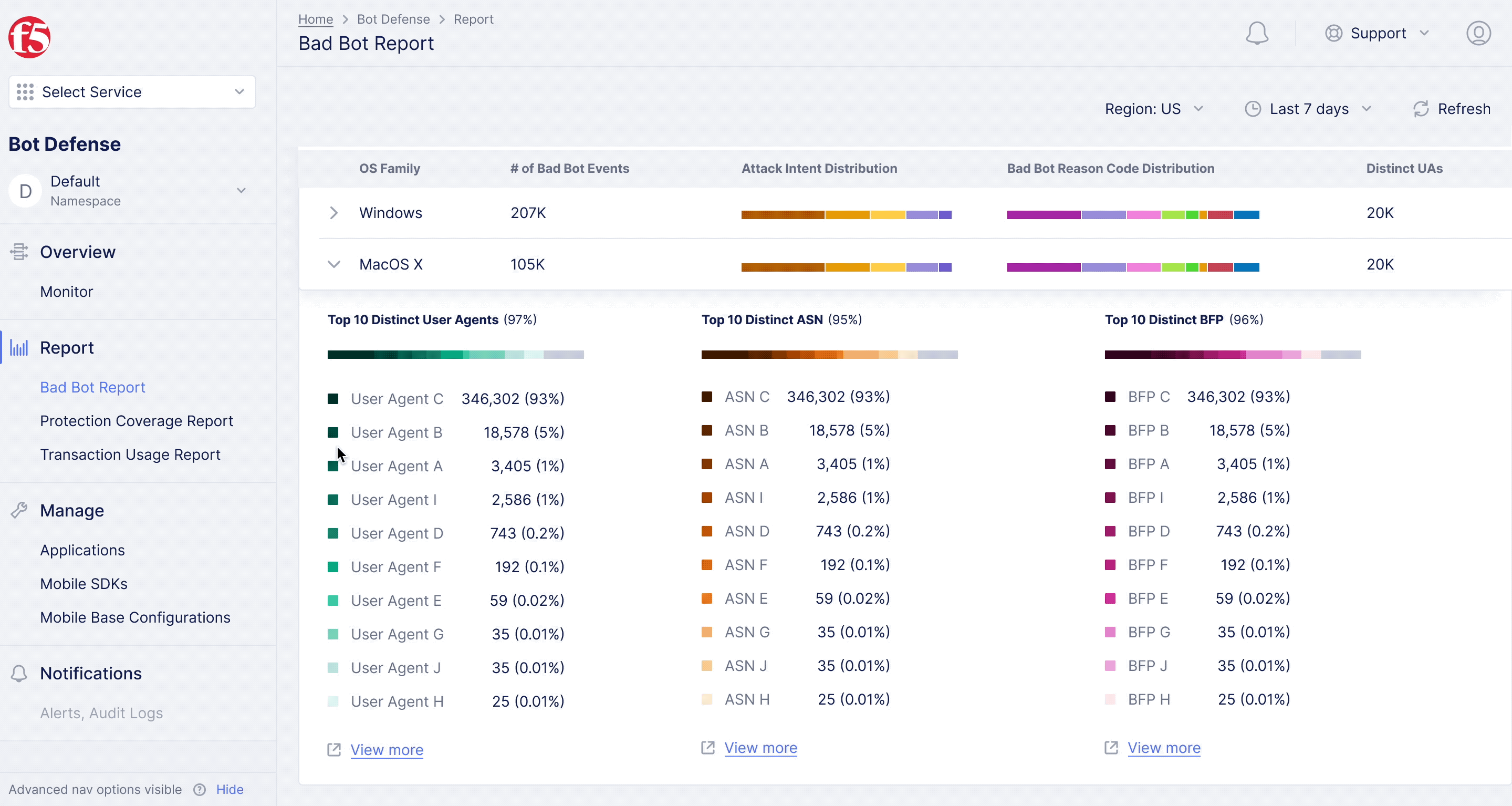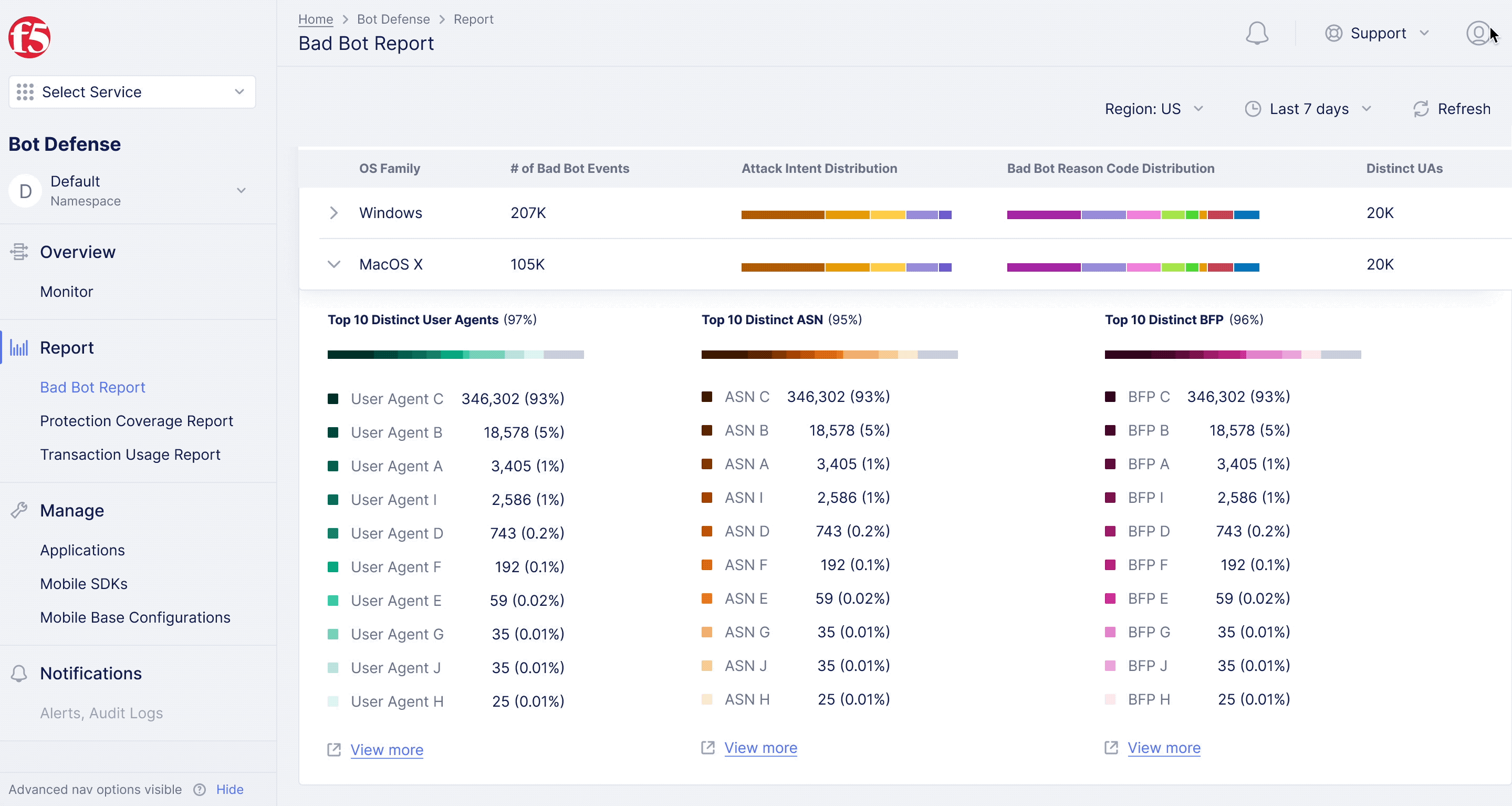
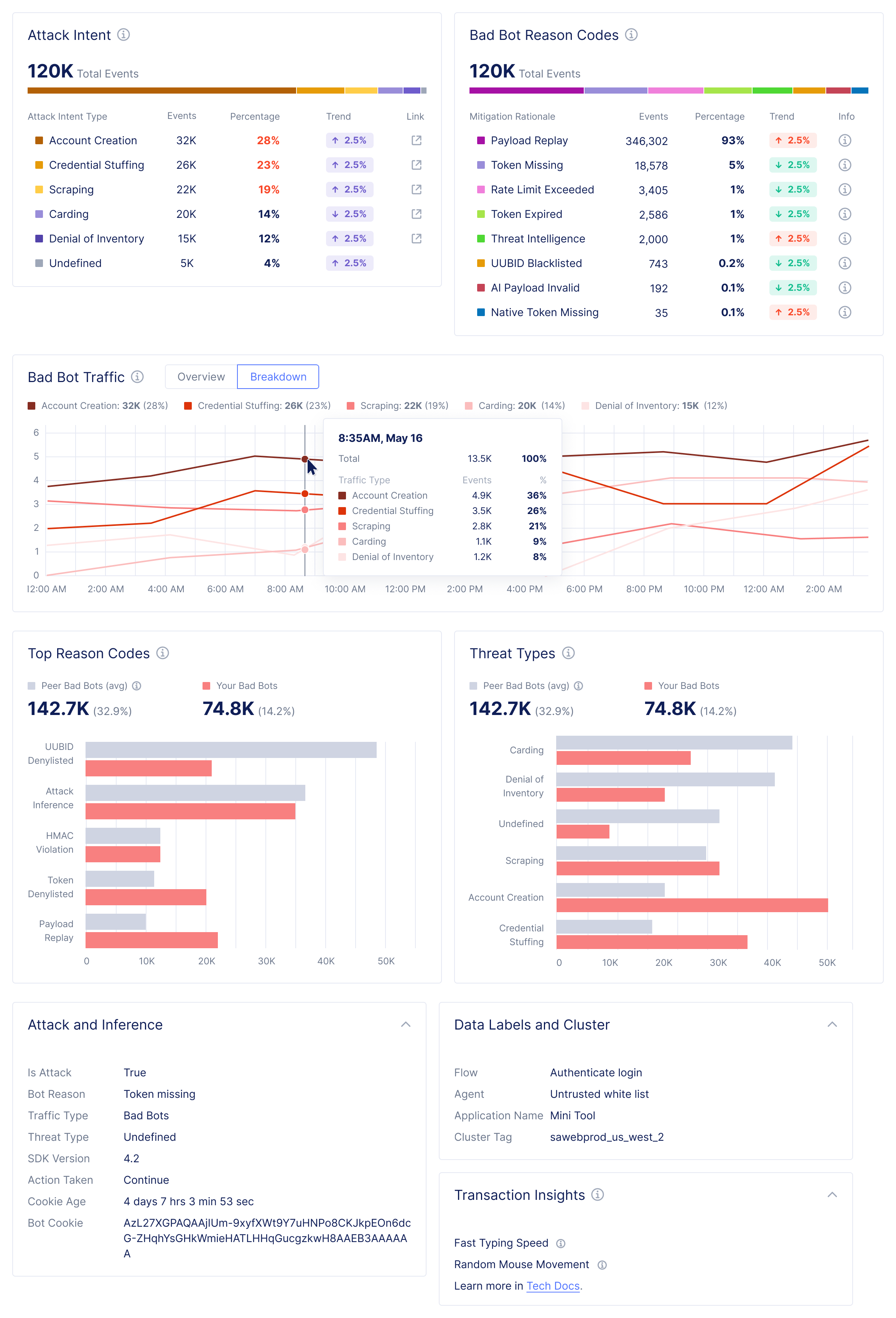
F5XC Bot Defense – Bad Bot Report
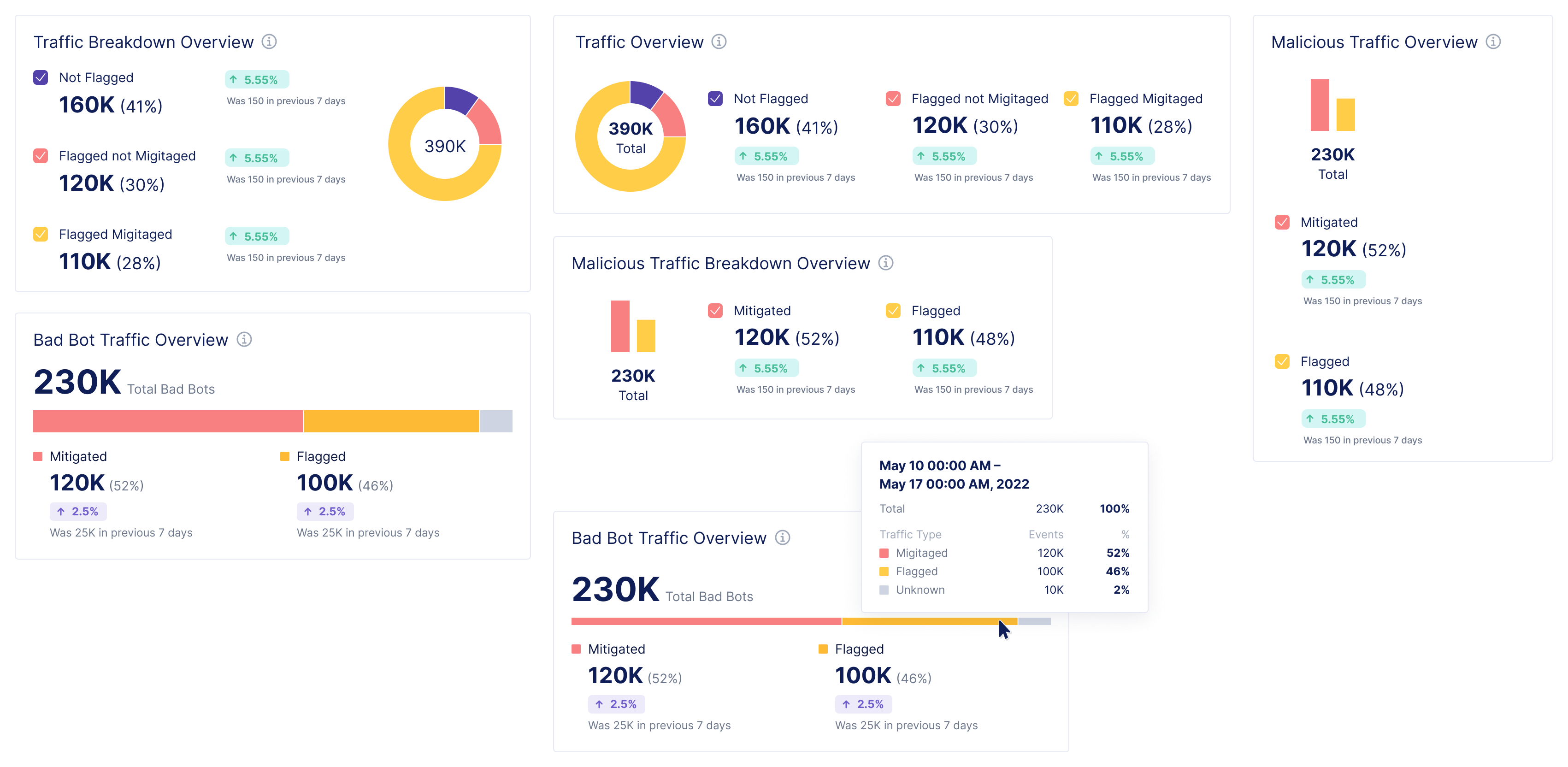
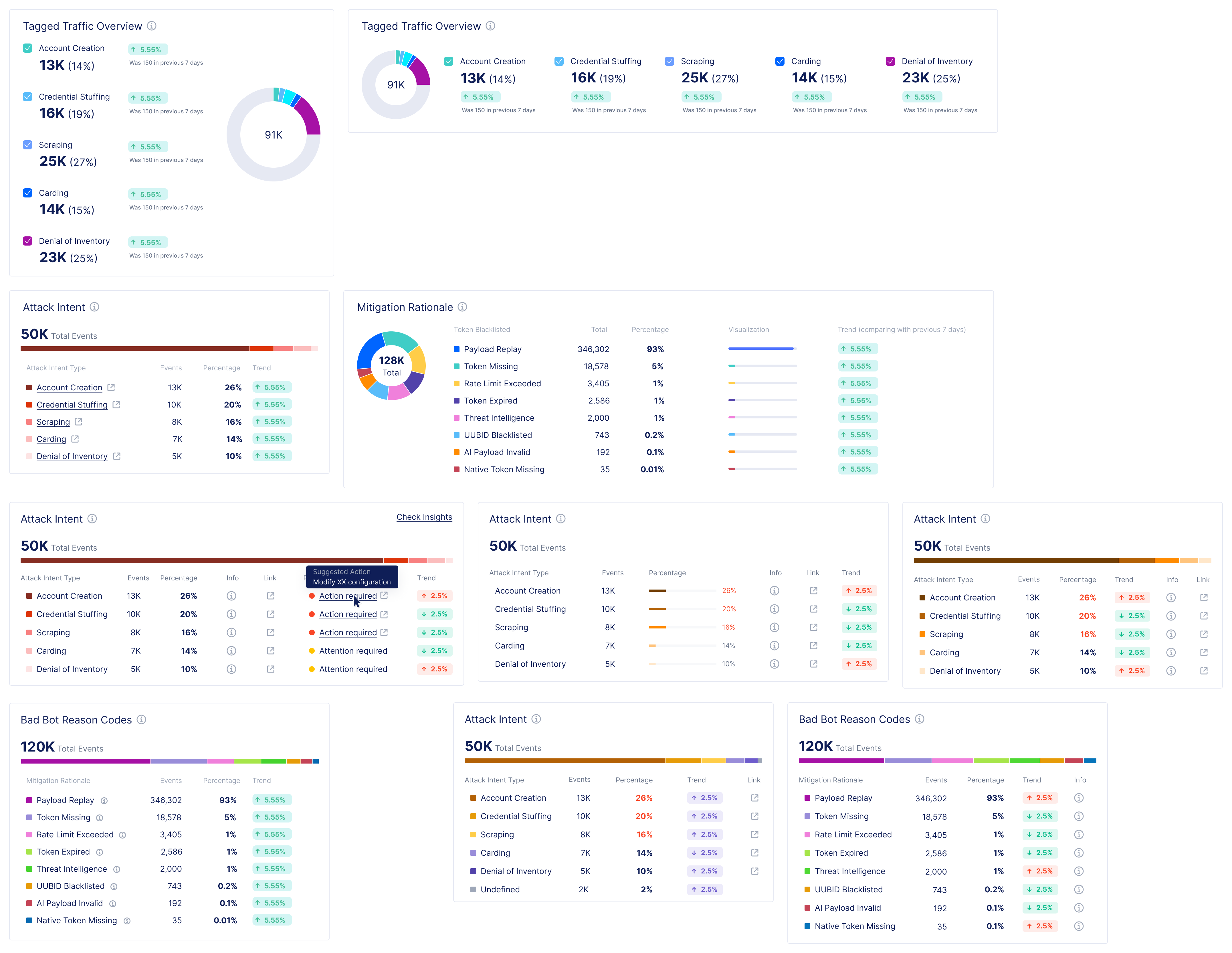
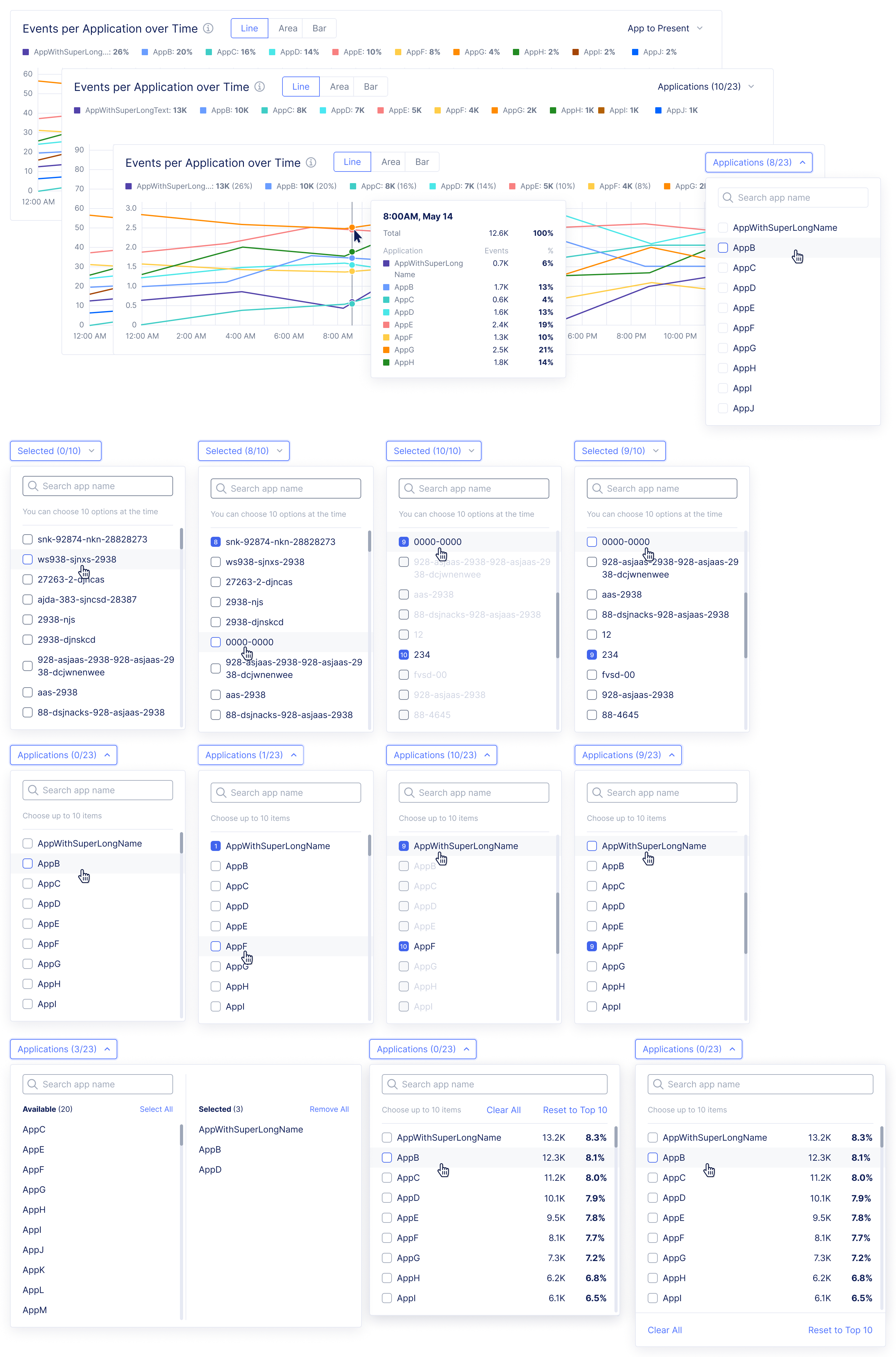
Diving deeper into analytics for bot defense.
Project Type: |
UX Designer at F5 |
Duration: |
Sep. – Oct. 2022, Jan. – Mar. 2023 |
Members: |
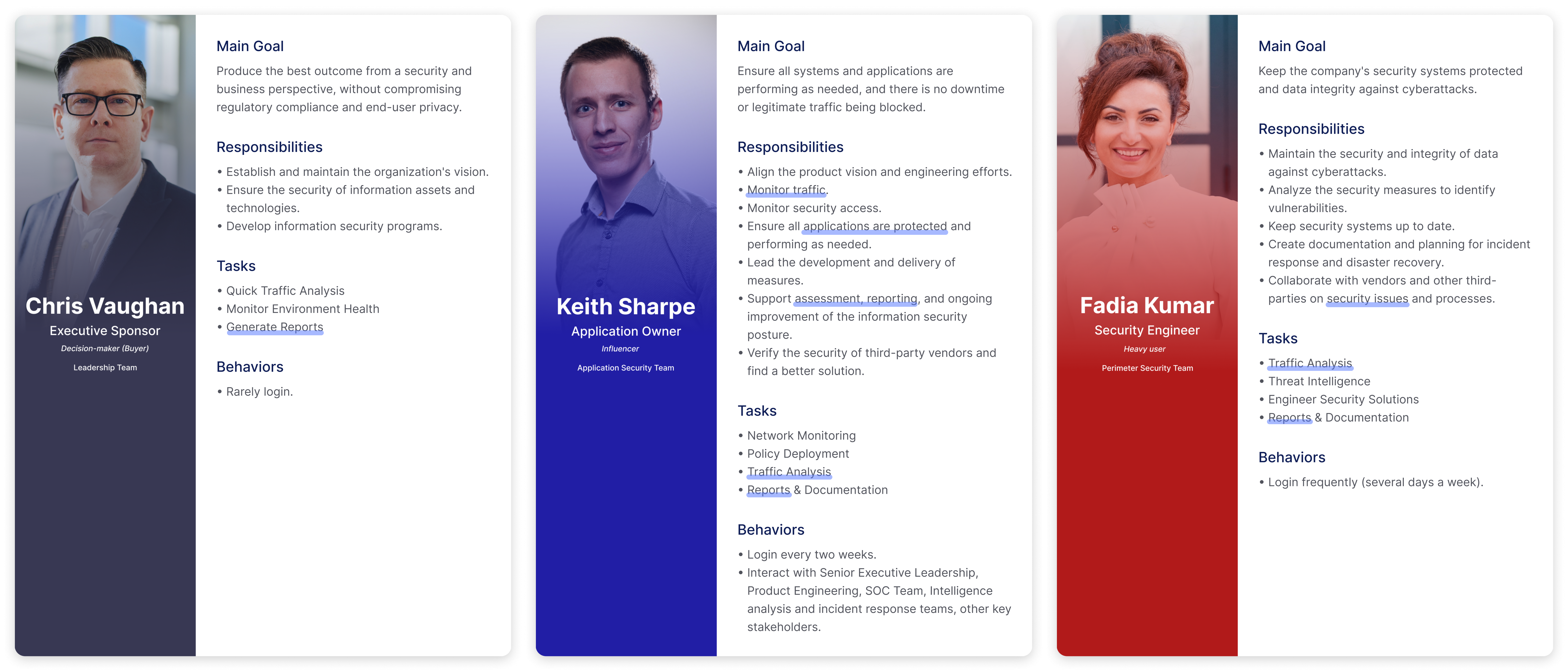
5 designers, 7 developers, 1 PM, 3 data scientists, 1 data visualization engineer, 2 security support engineers, 1 solution architect, 1 consulting manager, 2 technical account managers |
Practice Areas: |
UX design, information architecture, interaction design, information visualization |
My Role: |
I served as a UX design lead and co-worked closely with PM and multiple project stakeholders. |